Simplest encryption or parsing of the Road Rash 3 password structure by bone
Good afternoon, dear users.
Yes, yes, the title did not deceive you: today we will recall the good old console game Road Rash 3.
I think many of you remember with pleasure how you sat for hours in proud solitude or in a noisy company of friends, reeling virtual kilometers in this, without exaggeration, cult game. I also decided to remember youth one evening and go through a couple of levels in my favorite races. And so, armed with an emulator and a gamepad, he began climbing the career ladder. Everything was going great, but at one point something in the game was overwhelmed and she refused to take me to a new level, although all the conditions for this were fulfilled. I was not upset for a long time, because I knew that the game has a kind of password system for saving accumulated achievements. It was necessary only to “tweak” the existing password a bit with a typing method in order to manually transfer oneself to a new ill-fated level and continue the competition with a clear conscience.
But it was too easy and, frankly, not interesting. I immediately flashed the thought: "How does it work?" And I got excited about the idea of finding out the password generation algorithm itself, in order to be able to create it myself later on the basis of specific needs or just a mood.
So what is Road Rash 3? This is a race on the coolest sport motorcycles on the roads of various countries under the magnificent 8-bit music. The higher the place you occupy in the race, the more money you get, which you can then spend to buy a new iron horse or to upgrade it. Of particular interest is the opportunity to fight with rivals right during the drive at high speed, to take away from them a new weapon and use it to beat unlucky competitors even more. Description of the description, but we move closer to the numbers.
')
In the bottom line, we have the following game parameters:
Now take a look at the password itself:

Only 8 positions for characters. Each character can take the values 0-9 and AV. Total we get 32 possible characters in each position.
So let's get started.
I will not bore you with long stories about how I derived all these dependencies and algorithms, having spent many hours on experiments, I will go straight to the point.
Perhaps, many of you thought: “How can we fit so many parameters into such a small password?”, Is very simple. It is all about cunning logic and intricate algorithms. Then you will see how this happens.

The first 4 positions of the password are responsible for the money.
C440 xxxx
But not everything is so simple and obvious. There are some tricks.
1 and 2 positions are responsible for amounts up to $ 2,550 inclusive, 3 and 4 positions - for amounts above $ 2,550.
For example, if we have the sum of $ 5500 it (2 * $ 2560 + $ 380).
So, for 2 * $ 2,560 = $ 5,120, 3 and 4 positions will be responsible, and for the remainder in the form of $ 380 - 1 and 2 positions.
Now we dig deep into, continuing to consider our example. How are these $ 380 stored in 1 and 2 positions? It happens as follows.
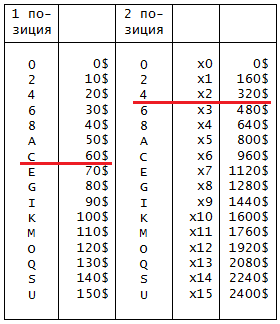
Table 1. 1 and 2 password positions - small money
1 position is responsible for amounts from $ 0 to $ 150 inclusive in increments of $ 10.
Similarly with the 2 position. Only now each step does not add $ 10, but increases by 1 a factor for $ 160. Those. how many times do we need to take $ 160 each: 0, 1, 2, etc.
To present "on the fingers" it can be as follows. We have $ 10, we add 10 more in it, 10 more, and so on, until we reach 150. All this time, we only have a character in 1 position. As we reached 150, we add 10 more and jump to the second position, which will already be 160. Next, adding 10, we will again rotate the character in the first position until we reach 150 and again jump to 2 position, where 160 will already be + 160 = 320.
Looking at the table, you can see that only even characters are taken (0, 2, 4 ...). For what? More on this later.
Thus, we can cover any amount in the range of $ 2550.
Let's look at the rest of the example above: $ 380 = 2 * $ 160 + $ 60.
$ 60 - the first position (less than $ 160). This sum corresponds to the symbol " C ".
2 * $ 160 - the second position. This sum corresponds to the symbol " 4 ".
That is, the amount of $ 380 can be written as " C4 ".
Here, in general, everything is similar.
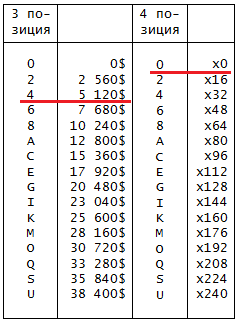
Table 2. 3 and 4 password positions - big money
Each even character of 3 positions gives + $ 2560 and so on up to $ 38,400 = $ 15 * $ 2,560.
Each even character of the 4 position is a multiplier for $ 40960 = 16 * $ 2560, i.e. how many times you need to take $ 40960: 0, 1, 2, etc. (this is a slightly simplified algorithm for the 4 position and we will return to it later).
Thus, we cover any amount from $ 2560 to $ 655350.
In our example, we have $ 5120 left. This, as you can see, is less than $ 40960, so the 4th position remains zero (we need to take zero $ 40960 times). Well, the symbol of 3 positions, corresponding to $ 5120 = $ 2,660 is “ 4 ” (see Table 2).
As a result, we received a combination of " C440 " for the first four positions, describing the amount of $ 5500.

With level everything is very simple and transparent. The 5 position of the password and only 5 characters are responsible for it:
xxxx 1 xxx
1 - the first level;
2 - the second level;
3 - the third level;
4 - the fourth level;
5 - the fifth level;
Improvements, as you remember, we have only four.
In the algorithm, they are logically divided into 2 groups:
Let's return to the 1st and 2nd positions of the password. Remember, earlier I mentioned that symbols for money are taken through one, i.e. only even? This is one of the secrets.
If we want to set performance for ourselves, then we need to increase the symbol in 1 position by one, and if we want to install the suspension, then we need to increase by one symbol in 2 positions.
C4 xx xxxx
Thus, we use the “window” formed by skipping odd symbols, which allows us, with the same amount, to have both the improvement and not the improvement.
Let's take a closer look at an example.
Our first two characters - " C4 " correspond to the sum of $ 380 and the lack of upgrades.
Do you want a brand new engine? No problem! Increase the character in 1 position by one and get " D4 ". In this case, the amount of money has not changed! It will change only with an increase of one more, i.e. to “ E4 ” (see Table 1).
Similarly, with the suspension: we increase the symbol in 2 positions by one and get " D5 ". The amount remained the same: $ 380.
As I mentioned above, they are registered in 5 positions (level). But this time the algorithm is slightly different.
The fact of tires (tires) increases the symbol in 5 positions by 8. The presence of protection increases the same symbol by 16.
Consider the situation for level 1:
Thus, it turns out that 1, 2 and 5 password positions are responsible for the improvements.
C4 xx 1 xxx
In total at level of 5 routes, they can be passed in any sequence.
For this parameter, we have a character in the 7 position of the password.
xxxx xx E x
It is logical to assume that the fact of passing a specific route is marked by some flag and is set to 0 or 1 for it (passed / not passed).
From all our 5 tracks, it is easy to compose a regular binary number, reflecting all possible combinations of passed and not passed routes.
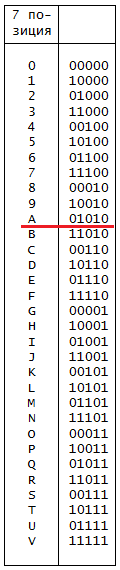
Table 3. 7 position password - traces passed
Here, each digit is responsible for one of 5 tracks. For example, 01010 shows that 1, 3 and 5 routes are not passed, and 2 and 4 - are passed.
Now, projecting this binary number on our alphanumeric character string, we get the corresponding character for the 7th position of the password. In our case, this is the character " A ".
And now let's get down to the most difficult thing - a motorcycle.
In this case, 3 positions are tied at once (3, 4 and 6) according to a rather intricate algorithm.
xx 40 x 1 xx
I will try to explain it as simply as possible.
The bike itself is not very difficult to choose. There are 16 of them and the 6th position in the password is responsible for them.
xxxx x B xxx
Here, as before in money, the symbols jump over one and are grouped in pairs.

Table 4. 6 position password - motorcycle
For example, 0 and 1 - the first motorcycle, 2 and 3 - the second, 4 and 5 - the third, etc. to end. The whole difficulty lies in determining which of the two characters to choose from a particular pair.
In order to understand the sequence of actions, go back to the 3 and 4 positions.
3 position can be represented only by even characters (0, 2, 4, 6, etc.). Odd here can not be, in principle, under any circumstances. But the characters 4 positions, as well as the sixth (motorcycle) are grouped in pairs: 0 and 1 - 0 $, 2 and 3 - $ 40960, 4 and 5 - 2 * $ 40960, etc. (earlier, when explaining 4 positions I talked about the simplification that I made there for simplicity; now you see the big picture).
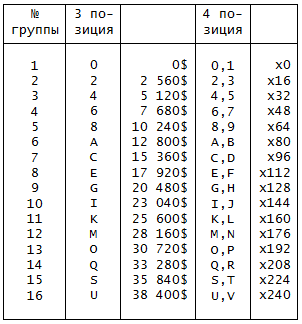
Table 5. 3 and 4 password positions - big money (full version)
Thus, we face 2 tasks:
The developers took the soul to glory and made as many as four masks to choose a motorcycle. You see them below in the image.
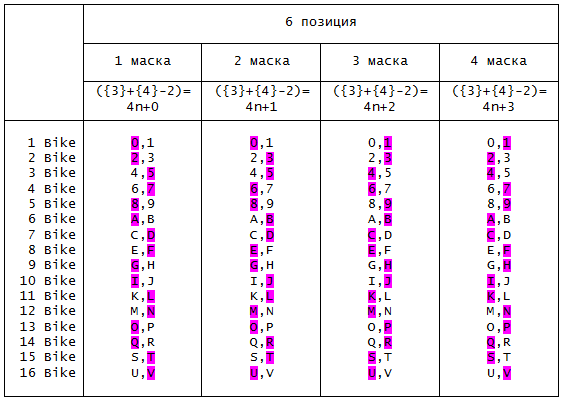
Table 6. Mask for the 6 position of the password (motorcycle)
Violet highlighted those characters that should be selected for the corresponding group (motorcycle). For example, if we hit the 3 mask and want to choose a 10 motorcycle, then we must take the "J" symbol for the 6th position of the password.
Now about how we need to choose the mask itself.
It can be noted that this mask as if rises one cell as its number increases. Those. mask number 2 is none other than mask number 1, shifted up by one position. The mask depends on 3 and 4 password positions. You can rightly ask: “How will it depend on position 4, if we have not yet decided which of the two symbols to substitute there?” - it’s very simple: it doesn’t depend on the symbol itself, but on the group of symbols, t. e. 0 and 1 - the first group, 2 and 3 - the second group, etc. (see Table 5). The same group also has the characters of the 3 position, only there it consists of one character, since there are no odd characters in general: 0 - the first group, 2 - the second, etc. The number of this group can be viewed in the first column of table 5.
Now the arithmetic itself: you need to calculate the expression
{3} + {4} - 2 ,
where {3} and {4} are numbers, respectively, groups of symbols for the 3rd and 4th positions (see Table 5).
If it is a multiple of 4, then we choose the first mask, if the remainder of division by 4n (n is a positive integer) is equal to 1, then we choose the second mask, if 2 is the third, and if 3 is the fourth.
Returning to our example, we had “ 40 ” positions 3 and 4.
4 - the third group, 0 - the first (see Table. 5).
We have {3} + {4} - 2 = 3 + 1 - 2 = 2.
The remainder of dividing by 4n is 2, which means we choose 3 mask for the motorcycle.
Thus, for 5 motorcycles, we have the symbol " 9 " in 6 positions of the password.
We have the last step, namely the choice of one of two characters for the 4 position. Here came the hitch ... My brain was already boiling from trying to explain it simply and clearly. It is not explained as such ...
In general, look.

Table 7. Selecting a character for 4 positions of the password
Let's look at any of the 4 masks, for example, the first one, namely, its purple part. The characters are grouped in two groups: purple, purple underneath, right shift, again 2 purple ones under each other, left shift, again 2 purple ones under each other, and so on. So, imagine that each first character in this group corresponds to one, and each second - two. Looking at the first mask from top to bottom: 1, 2, 1, 2, 1, 2 ... With the second one it will be like this: 2, 1, 2, 1, 2, etc. The essence, I hope, is clear. Why are these ones and twos? But to what. In our example, we choose a character in the fourth position from 0 and 1 (remember, 3 and 4 characters are 40 for us; 4 will always be itself, but 0 is not yet final: it can be either 0 or 1 (see Table 5)). We also know that we have a third mask (we have calculated the expression above). Therefore, we look at the 3 mask and find our group in it (0 and 1) - it is the first from above. To her, as we have just considered, corresponds to one, it means we take the first character from this group, i.e. " 0 ".
Consider another example for cleanliness: we work with the second mask and the character for the 4th position is selected from C and D. We look at the 2 mask: C and D are second in the purple vertical block, it means we choose the second character, i.e. " D ".
For a snack, we have 8 position.
xxxx xxx M
It's all pretty obvious - this is a checksum. Changing each of the first seven positions affects it in some way. Unfortunately, I can not give the algorithms for its calculation. And so much time was spent on figuring out the mechanism of work, moreover there would be even more theory. And I'm afraid the article has already stretched to indecent size. So let's just take for the fact that there is a checksum located, somehow dependent on the first seven positions of the password.
Congratulations, you are a real hero, if you actually read this far and still understood something;)
It turned out to be terribly difficult to explain everything on paper and it turned out incoherent nonsense, but in fact the theory is rather easy if you think a little and try to understand it. I tried as best I could to show everything very simply and clearly. I hope at least a little bit of it happened to me. If something remains unclear to you, ask questions in the comments - I will answer.
The algorithms given here will help to understand the basics of encryption in practice, and generally satisfy people's interest: “But how does it work?” And also, I hope, the article will be interesting to read to people who are nostalgic for the times of their favorite 16-bit races on sega.
And finally, a small bonus. He made a password generator in case anyone wants to play.
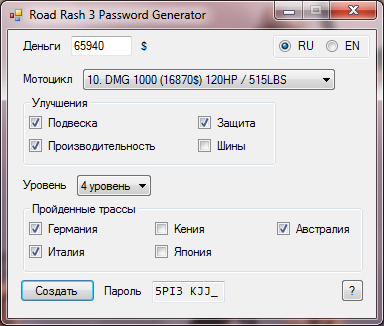
Download
Download 2
Download 3
8 characters, like you, I hope, have already read above, no, but quickly manually sorting through a maximum of 32 variants is not difficult for it.
PS In order to play sega on a computer, an emulator is required (I use WGens) and the rum of the game itself. All without problems is on the Internet.
PPS Congratulations to all Russians and our neighbors on the victory in voting for the right to host the World Cup in 2018!
Thank you for your attention and see you again in the vastness of Habr!
Yes, yes, the title did not deceive you: today we will recall the good old console game Road Rash 3.

I think many of you remember with pleasure how you sat for hours in proud solitude or in a noisy company of friends, reeling virtual kilometers in this, without exaggeration, cult game. I also decided to remember youth one evening and go through a couple of levels in my favorite races. And so, armed with an emulator and a gamepad, he began climbing the career ladder. Everything was going great, but at one point something in the game was overwhelmed and she refused to take me to a new level, although all the conditions for this were fulfilled. I was not upset for a long time, because I knew that the game has a kind of password system for saving accumulated achievements. It was necessary only to “tweak” the existing password a bit with a typing method in order to manually transfer oneself to a new ill-fated level and continue the competition with a clear conscience.
But it was too easy and, frankly, not interesting. I immediately flashed the thought: "How does it work?" And I got excited about the idea of finding out the password generation algorithm itself, in order to be able to create it myself later on the basis of specific needs or just a mood.
A bit of theory
So what is Road Rash 3? This is a race on the coolest sport motorcycles on the roads of various countries under the magnificent 8-bit music. The higher the place you occupy in the race, the more money you get, which you can then spend to buy a new iron horse or to upgrade it. Of particular interest is the opportunity to fight with rivals right during the drive at high speed, to take away from them a new weapon and use it to beat unlucky competitors even more. Description of the description, but we move closer to the numbers.
')
In the bottom line, we have the following game parameters:
- the amount of money (from $ 0 to $ 655350 in increments of $ 10);
- motorcycle (one of 16 possible);
- improvements to it (4 improvements in various combinations);
- current level (one of 5 possible);
- trails on this level (5 runs in various combinations).
Now take a look at the password itself:

Only 8 positions for characters. Each character can take the values 0-9 and AV. Total we get 32 possible characters in each position.
The most interesting
So let's get started.
I will not bore you with long stories about how I derived all these dependencies and algorithms, having spent many hours on experiments, I will go straight to the point.
Perhaps, many of you thought: “How can we fit so many parameters into such a small password?”, Is very simple. It is all about cunning logic and intricate algorithms. Then you will see how this happens.
Money, money and more money

The first 4 positions of the password are responsible for the money.
C440 xxxx
But not everything is so simple and obvious. There are some tricks.
1 and 2 positions are responsible for amounts up to $ 2,550 inclusive, 3 and 4 positions - for amounts above $ 2,550.
For example, if we have the sum of $ 5500 it (2 * $ 2560 + $ 380).
So, for 2 * $ 2,560 = $ 5,120, 3 and 4 positions will be responsible, and for the remainder in the form of $ 380 - 1 and 2 positions.
Let's start small: 1 and 2 positions and amounts less than $ 2550
Now we dig deep into, continuing to consider our example. How are these $ 380 stored in 1 and 2 positions? It happens as follows.

Table 1. 1 and 2 password positions - small money
1 position is responsible for amounts from $ 0 to $ 150 inclusive in increments of $ 10.
Similarly with the 2 position. Only now each step does not add $ 10, but increases by 1 a factor for $ 160. Those. how many times do we need to take $ 160 each: 0, 1, 2, etc.
To present "on the fingers" it can be as follows. We have $ 10, we add 10 more in it, 10 more, and so on, until we reach 150. All this time, we only have a character in 1 position. As we reached 150, we add 10 more and jump to the second position, which will already be 160. Next, adding 10, we will again rotate the character in the first position until we reach 150 and again jump to 2 position, where 160 will already be + 160 = 320.
Looking at the table, you can see that only even characters are taken (0, 2, 4 ...). For what? More on this later.
Thus, we can cover any amount in the range of $ 2550.
Let's look at the rest of the example above: $ 380 = 2 * $ 160 + $ 60.
$ 60 - the first position (less than $ 160). This sum corresponds to the symbol " C ".
2 * $ 160 - the second position. This sum corresponds to the symbol " 4 ".
That is, the amount of $ 380 can be written as " C4 ".
Now consider the 3 and 4 positions and the amount of more than $ 2550.
Here, in general, everything is similar.

Table 2. 3 and 4 password positions - big money
Each even character of 3 positions gives + $ 2560 and so on up to $ 38,400 = $ 15 * $ 2,560.
Each even character of the 4 position is a multiplier for $ 40960 = 16 * $ 2560, i.e. how many times you need to take $ 40960: 0, 1, 2, etc. (this is a slightly simplified algorithm for the 4 position and we will return to it later).
Thus, we cover any amount from $ 2560 to $ 655350.
In our example, we have $ 5120 left. This, as you can see, is less than $ 40960, so the 4th position remains zero (we need to take zero $ 40960 times). Well, the symbol of 3 positions, corresponding to $ 5120 = $ 2,660 is “ 4 ” (see Table 2).
As a result, we received a combination of " C440 " for the first four positions, describing the amount of $ 5500.
Level

With level everything is very simple and transparent. The 5 position of the password and only 5 characters are responsible for it:
xxxx 1 xxx
1 - the first level;
2 - the second level;
3 - the third level;
4 - the fourth level;
5 - the fifth level;
Improvements (upgrades)
Improvements, as you remember, we have only four.

In the algorithm, they are logically divided into 2 groups:
- performance and suspension (performance and suspension);
- protection and tires (protection and tires).
First about the first couple
Let's return to the 1st and 2nd positions of the password. Remember, earlier I mentioned that symbols for money are taken through one, i.e. only even? This is one of the secrets.
If we want to set performance for ourselves, then we need to increase the symbol in 1 position by one, and if we want to install the suspension, then we need to increase by one symbol in 2 positions.
C4 xx xxxx
Thus, we use the “window” formed by skipping odd symbols, which allows us, with the same amount, to have both the improvement and not the improvement.
Let's take a closer look at an example.
Our first two characters - " C4 " correspond to the sum of $ 380 and the lack of upgrades.
Do you want a brand new engine? No problem! Increase the character in 1 position by one and get " D4 ". In this case, the amount of money has not changed! It will change only with an increase of one more, i.e. to “ E4 ” (see Table 1).
Similarly, with the suspension: we increase the symbol in 2 positions by one and get " D5 ". The amount remained the same: $ 380.
Now about the second pair of upgrades
As I mentioned above, they are registered in 5 positions (level). But this time the algorithm is slightly different.
The fact of tires (tires) increases the symbol in 5 positions by 8. The presence of protection increases the same symbol by 16.
Consider the situation for level 1:
- Level 1 without improvements: xxxx 1 xxx;
- Level 1 with tires: xxxx 9 xxx (+8);
- Level 1 with protection: xxxx H xxx (+16);
- Level 1 with tires and protection: xxxx P xxx (+ 8 + 16);
Thus, it turns out that 1, 2 and 5 password positions are responsible for the improvements.
C4 xx 1 xxx
Completed trails
In total at level of 5 routes, they can be passed in any sequence.

For this parameter, we have a character in the 7 position of the password.
xxxx xx E x
It is logical to assume that the fact of passing a specific route is marked by some flag and is set to 0 or 1 for it (passed / not passed).
From all our 5 tracks, it is easy to compose a regular binary number, reflecting all possible combinations of passed and not passed routes.

Table 3. 7 position password - traces passed
Here, each digit is responsible for one of 5 tracks. For example, 01010 shows that 1, 3 and 5 routes are not passed, and 2 and 4 - are passed.
Now, projecting this binary number on our alphanumeric character string, we get the corresponding character for the 7th position of the password. In our case, this is the character " A ".
Motorcycle and some more money
And now let's get down to the most difficult thing - a motorcycle.
In this case, 3 positions are tied at once (3, 4 and 6) according to a rather intricate algorithm.
xx 40 x 1 xx
I will try to explain it as simply as possible.
The bike itself is not very difficult to choose. There are 16 of them and the 6th position in the password is responsible for them.
xxxx x B xxx
Here, as before in money, the symbols jump over one and are grouped in pairs.

Table 4. 6 position password - motorcycle
For example, 0 and 1 - the first motorcycle, 2 and 3 - the second, 4 and 5 - the third, etc. to end. The whole difficulty lies in determining which of the two characters to choose from a particular pair.
In order to understand the sequence of actions, go back to the 3 and 4 positions.
3 position can be represented only by even characters (0, 2, 4, 6, etc.). Odd here can not be, in principle, under any circumstances. But the characters 4 positions, as well as the sixth (motorcycle) are grouped in pairs: 0 and 1 - 0 $, 2 and 3 - $ 40960, 4 and 5 - 2 * $ 40960, etc. (earlier, when explaining 4 positions I talked about the simplification that I made there for simplicity; now you see the big picture).

Table 5. 3 and 4 password positions - big money (full version)
Thus, we face 2 tasks:
- choose one of two possible characters for the 4 position;
- choose one of two possible characters for 6 positions.
First of all, let's deal with a motorcycle
The developers took the soul to glory and made as many as four masks to choose a motorcycle. You see them below in the image.

Table 6. Mask for the 6 position of the password (motorcycle)
Violet highlighted those characters that should be selected for the corresponding group (motorcycle). For example, if we hit the 3 mask and want to choose a 10 motorcycle, then we must take the "J" symbol for the 6th position of the password.
Now about how we need to choose the mask itself.
It can be noted that this mask as if rises one cell as its number increases. Those. mask number 2 is none other than mask number 1, shifted up by one position. The mask depends on 3 and 4 password positions. You can rightly ask: “How will it depend on position 4, if we have not yet decided which of the two symbols to substitute there?” - it’s very simple: it doesn’t depend on the symbol itself, but on the group of symbols, t. e. 0 and 1 - the first group, 2 and 3 - the second group, etc. (see Table 5). The same group also has the characters of the 3 position, only there it consists of one character, since there are no odd characters in general: 0 - the first group, 2 - the second, etc. The number of this group can be viewed in the first column of table 5.
Now the arithmetic itself: you need to calculate the expression
{3} + {4} - 2 ,
where {3} and {4} are numbers, respectively, groups of symbols for the 3rd and 4th positions (see Table 5).
If it is a multiple of 4, then we choose the first mask, if the remainder of division by 4n (n is a positive integer) is equal to 1, then we choose the second mask, if 2 is the third, and if 3 is the fourth.
Returning to our example, we had “ 40 ” positions 3 and 4.
4 - the third group, 0 - the first (see Table. 5).
We have {3} + {4} - 2 = 3 + 1 - 2 = 2.
The remainder of dividing by 4n is 2, which means we choose 3 mask for the motorcycle.
Thus, for 5 motorcycles, we have the symbol " 9 " in 6 positions of the password.
Final spurt
We have the last step, namely the choice of one of two characters for the 4 position. Here came the hitch ... My brain was already boiling from trying to explain it simply and clearly. It is not explained as such ...
In general, look.

Table 7. Selecting a character for 4 positions of the password
Let's look at any of the 4 masks, for example, the first one, namely, its purple part. The characters are grouped in two groups: purple, purple underneath, right shift, again 2 purple ones under each other, left shift, again 2 purple ones under each other, and so on. So, imagine that each first character in this group corresponds to one, and each second - two. Looking at the first mask from top to bottom: 1, 2, 1, 2, 1, 2 ... With the second one it will be like this: 2, 1, 2, 1, 2, etc. The essence, I hope, is clear. Why are these ones and twos? But to what. In our example, we choose a character in the fourth position from 0 and 1 (remember, 3 and 4 characters are 40 for us; 4 will always be itself, but 0 is not yet final: it can be either 0 or 1 (see Table 5)). We also know that we have a third mask (we have calculated the expression above). Therefore, we look at the 3 mask and find our group in it (0 and 1) - it is the first from above. To her, as we have just considered, corresponds to one, it means we take the first character from this group, i.e. " 0 ".
Consider another example for cleanliness: we work with the second mask and the character for the 4th position is selected from C and D. We look at the 2 mask: C and D are second in the purple vertical block, it means we choose the second character, i.e. " D ".
At last
For a snack, we have 8 position.
xxxx xxx M
It's all pretty obvious - this is a checksum. Changing each of the first seven positions affects it in some way. Unfortunately, I can not give the algorithms for its calculation. And so much time was spent on figuring out the mechanism of work, moreover there would be even more theory. And I'm afraid the article has already stretched to indecent size. So let's just take for the fact that there is a checksum located, somehow dependent on the first seven positions of the password.
Instead of conclusion
Congratulations, you are a real hero, if you actually read this far and still understood something;)
It turned out to be terribly difficult to explain everything on paper and it turned out incoherent nonsense, but in fact the theory is rather easy if you think a little and try to understand it. I tried as best I could to show everything very simply and clearly. I hope at least a little bit of it happened to me. If something remains unclear to you, ask questions in the comments - I will answer.
What is this article for and who needs it?
The algorithms given here will help to understand the basics of encryption in practice, and generally satisfy people's interest: “But how does it work?” And also, I hope, the article will be interesting to read to people who are nostalgic for the times of their favorite 16-bit races on sega.
And finally, a small bonus. He made a password generator in case anyone wants to play.

Download
Download 2
Download 3
8 characters, like you, I hope, have already read above, no, but quickly manually sorting through a maximum of 32 variants is not difficult for it.
PS In order to play sega on a computer, an emulator is required (I use WGens) and the rum of the game itself. All without problems is on the Internet.
PPS Congratulations to all Russians and our neighbors on the victory in voting for the right to host the World Cup in 2018!
Thank you for your attention and see you again in the vastness of Habr!
Source: https://habr.com/ru/post/108728/
All Articles