Peripeteia detection and unpacking
Hello!
Analyzing the work of the recently appeared Sality.bh , I discovered an interesting moment with the detection of its components, which I would like to talk about. Truly, the ways of the Virlabs are inscrutable! :)
So, during the system infection, this representative of the Sality family creates a series of malicious files in the% temp% directory with the functionality of stealing passwords and providing unauthorized access to the system over the network.
At the same time, a slightly obfuscated autorun.inf is created on each disk (it, of course, is hidden from the user):
and also the little body of the malware packed by Safeguard 1.03 -> Simonzh.
')
At the same time, the author is not very worried about backdoors / passvord steelers, since they are packaged much easier - using UPX.
It would seem that everything is normal and logical. Only the lack of logic caused me that in order to work with the packaged backdoor I had to disable the antivirus, and with the unpacked one - no.
It turned out that everything is simple - the UPX-packed version has a stable detection from a number of products , for example, Kaspersky confidently considers it Backdoor.Win32.Mazben.es. But unpacked is already safe according to Kaspersky, moreover - it is completely different according to some antiviruses .
I tried to make a table reflecting the picture. Unfortunately, for some reason, VirusTotal in one case displayed, and in the other - there is no information of the following antiviruses: BitDefender, Authentium, Command, FSecure, GData, nProtect, Sunbelt, VIPRE. For this reason, they are not included in the table. So, the result:
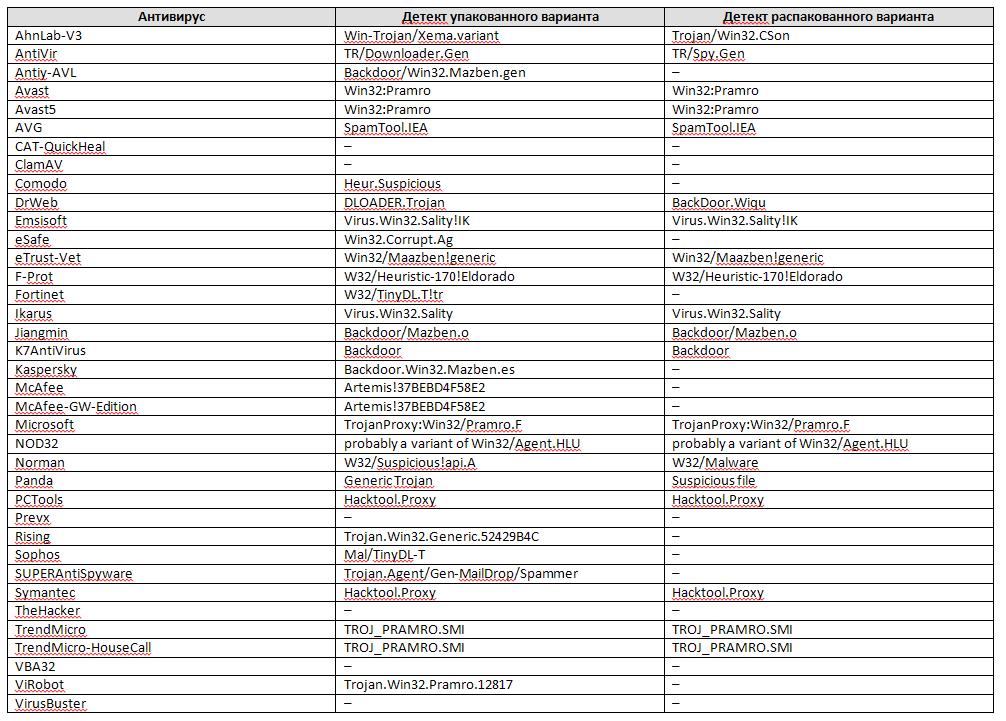
Interestingly, Avast, AVG, Emsisoft, E-Trust-Vet, F-Prot (though only for heuristics), Ikarus, Jiangmin, Microsoft, NOD32 (also heuristics), PCTools, Symantec and TrendMicro . At the same time, Emsisoft and Ikarus do not quite correctly consider this file as a representative of Sality, in fact it is one of the implemented modules, lacking the ability to infect files.
Antiy-AVL, Comodo (although there was a detector here only on heuristics), eSafe, Fortinet, Kaspersky, McAfee, Rising, Sophos, SUPERAntiSpyware, ViRobot . For unknown reasons, these antiviruses (or specialists of these companies) detect the packed version, but do not detect the unpacked version. Is there no UPX unpacking procedure in the antivirus? I have no answer to this question.
PS This article does not discuss the effectiveness of the treatment of executable files affected by Sality.bh.
Analyzing the work of the recently appeared Sality.bh , I discovered an interesting moment with the detection of its components, which I would like to talk about. Truly, the ways of the Virlabs are inscrutable! :)
So, during the system infection, this representative of the Sality family creates a series of malicious files in the% temp% directory with the functionality of stealing passwords and providing unauthorized access to the system over the network.
At the same time, a slightly obfuscated autorun.inf is created on each disk (it, of course, is hidden from the user):
[AutoRun]
;LCrpr
open =qukai.exe
;sFhlFy IjHXVbXTuwvFsUusCbckP ICvmveywrEcK
Shell\exPlore\Command= qukai.exe
;xPRxeLQpYkF ajYOvwhXffjEul GuYigjuhVTq
shElL\Open\defAuLt=1
;eodORB
SheLl\oPen\COMmaND= qukai.exe
;yWvgURCkrpRrKuhxrUvCCjvbpKkD
SheLL\AuTOpLaY\ComManD= qukai.exe
and also the little body of the malware packed by Safeguard 1.03 -> Simonzh.
')
At the same time, the author is not very worried about backdoors / passvord steelers, since they are packaged much easier - using UPX.
It would seem that everything is normal and logical. Only the lack of logic caused me that in order to work with the packaged backdoor I had to disable the antivirus, and with the unpacked one - no.
It turned out that everything is simple - the UPX-packed version has a stable detection from a number of products , for example, Kaspersky confidently considers it Backdoor.Win32.Mazben.es. But unpacked is already safe according to Kaspersky, moreover - it is completely different according to some antiviruses .
I tried to make a table reflecting the picture. Unfortunately, for some reason, VirusTotal in one case displayed, and in the other - there is no information of the following antiviruses: BitDefender, Authentium, Command, FSecure, GData, nProtect, Sunbelt, VIPRE. For this reason, they are not included in the table. So, the result:

Interestingly, Avast, AVG, Emsisoft, E-Trust-Vet, F-Prot (though only for heuristics), Ikarus, Jiangmin, Microsoft, NOD32 (also heuristics), PCTools, Symantec and TrendMicro . At the same time, Emsisoft and Ikarus do not quite correctly consider this file as a representative of Sality, in fact it is one of the implemented modules, lacking the ability to infect files.
Antiy-AVL, Comodo (although there was a detector here only on heuristics), eSafe, Fortinet, Kaspersky, McAfee, Rising, Sophos, SUPERAntiSpyware, ViRobot . For unknown reasons, these antiviruses (or specialists of these companies) detect the packed version, but do not detect the unpacked version. Is there no UPX unpacking procedure in the antivirus? I have no answer to this question.
PS This article does not discuss the effectiveness of the treatment of executable files affected by Sality.bh.
Source: https://habr.com/ru/post/108456/
All Articles