New file virus with MMX instructions
Nguyen Ngoc Dung, a virus analyst at the Vietnamese computer security company Bkis, wrote in his blog about the emergence of a new type of file virus from the Sality family. At the moment, viruses of this family are among the most technologically advanced and widespread file viruses that infect the computers of Windows users.
This time the situation is interesting because in the metamorphic code of the virus there are some MMX instructions ( M ulti M edia e X tension) that were not previously used in any of the malware infectors.

Sality with MMX
')
Usually, all previous versions of Sality used only x86 codes, like other representatives of this type of malware. Today, x86 is emulated by most antivirus heuristics; accordingly, the introduction of MMX is intended to impede the work of emulators and avoid detection.
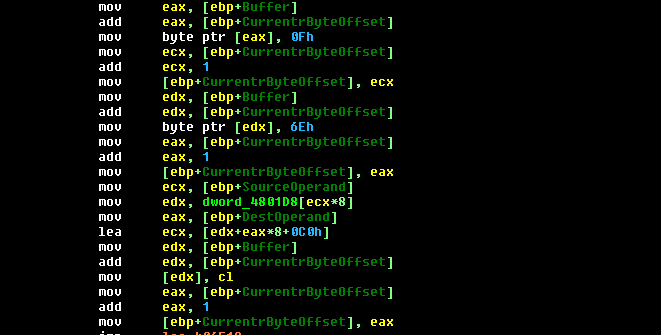
Generating MOVD instructions mm, r / m32
The virus code contains only a few MMX instructions. However, judging by the dynamics of malware development and the level of innovation, we should expect new versions to appear with a large number of MMX code. Moreover, in the new version of Sality, the part of the code that was characteristic of this malware and used in signatures has been modified while preserving its functionality, for example:
(R1 and R2 - 32-bit registers [] indicates a memory cell whose address is stored in the register)
Code changed to ::
or
or
Thus, it becomes even more difficult to determine which code serves to decrypt the virus component, and which one is ordinary garbage, which registers contain important information, and which simply confuse disassembly. This imposes more serious requirements on anti-virus programs.
Currently, the malware is detected by the following programs , in particular, the product of the authors BKAV detects it as W32.SalityVM.PE, and Kaspersky products - as Virus.Win32.Sality.bh.
Guaranteed to cure affected files can be a free utility SalityKiller from Kaspersky Lab .
UPD: To be fair, the malware was identified by KIS 2011 heuristics as Trojan.Win32.Generic, which fully corresponds to the functionality of the Sality family .
This time the situation is interesting because in the metamorphic code of the virus there are some MMX instructions ( M ulti M edia e X tension) that were not previously used in any of the malware infectors.

Sality with MMX
')
Usually, all previous versions of Sality used only x86 codes, like other representatives of this type of malware. Today, x86 is emulated by most antivirus heuristics; accordingly, the introduction of MMX is intended to impede the work of emulators and avoid detection.

Generating MOVD instructions mm, r / m32
The virus code contains only a few MMX instructions. However, judging by the dynamics of malware development and the level of innovation, we should expect new versions to appear with a large number of MMX code. Moreover, in the new version of Sality, the part of the code that was characteristic of this malware and used in signatures has been modified while preserving its functionality, for example:
R1 = [R2](R1 and R2 - 32-bit registers [] indicates a memory cell whose address is stored in the register)
Code changed to ::
R1= 0
R1 = R1 xor [R2]or
R1 = 0
R1 = R1 or [R2]or
R1 = 0
R1 = R1 + [R2]Thus, it becomes even more difficult to determine which code serves to decrypt the virus component, and which one is ordinary garbage, which registers contain important information, and which simply confuse disassembly. This imposes more serious requirements on anti-virus programs.
Currently, the malware is detected by the following programs , in particular, the product of the authors BKAV detects it as W32.SalityVM.PE, and Kaspersky products - as Virus.Win32.Sality.bh.
Guaranteed to cure affected files can be a free utility SalityKiller from Kaspersky Lab .
UPD: To be fair, the malware was identified by KIS 2011 heuristics as Trojan.Win32.Generic, which fully corresponds to the functionality of the Sality family .
Source: https://habr.com/ru/post/108034/
All Articles