VERIS website launched
 Verizon introduced the Veris Enterprise Risk and Incident Sharing website. The purpose of the service is to provide an opportunity to anonymously publish information about database corruption, attacks on social networks, cases of hacking of various sites and services.
Verizon introduced the Veris Enterprise Risk and Incident Sharing website. The purpose of the service is to provide an opportunity to anonymously publish information about database corruption, attacks on social networks, cases of hacking of various sites and services.Such incidents occur frequently, but rarely become public knowledge, as companies are in no hurry to report this, fearing the loss of Clients' trust and damage to their reputation. This behavior is understandable, but this leads to silencing security problems and hurts everyone.
The new service will allow anonymous reporting of a detailed description of security issues.
According to Alexander Hutton, head of research and intelligence at Verizon Business: “This will be in the interests of the entire community. Reliable data will help us all learn from mistakes. ”
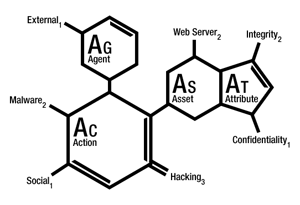
VERIS is an application and framework designed to streamline the information received in a structured language.
Documentation on the use of the framework is also presented , with several examples of use. I will give only the first.
Example 1 : SQL injection leading to malware infection
An attacker from a Russian IP address executed an attack using multiple SQL injections against a published web application. Actions allowed to introduce keyloggers and network sniffers to internal systems. Keyloggers intercepted several domain credentials, which the attackers used for subsequent penetration into the corporate network. Packet sniffer collected data for several months and the attacker periodically returned to collect the information stored by them.
')
The attack is divided into three separate events using the a 4 model (I suppose that no further translation is needed, the language is all the same):
Event 1
Agent: External (Type: Organized crime; Role: Participated directly and deliberately; Origin: Europe-East)
Action: Hacking (Type: SQLinjection; Path: Web Application)
Asset: Servers & Applications (Type: Web app/server, Database)
Attribute: Integrity
Event 2
Agent: External (Type: Organized crime; Role: Participated directly and deliberately; Origin: Europe-East)
Action: Malware (Type: Keylogger, Packet sniffer; Path: Installed / injected by remote attacker)
Asset: Servers & Applications (Type: Web app/server)
Attribute: Confidentiality
Event 3
Agent: External (Type: Organized crime; Role: Participated directly and deliberately; Origin: Europe-East)
Action: Hacking (Type: Use of stolen credentials; Path: Remote access and control services/software)
Asset: Servers & Applications, Networks & NW Devices (Type: multiple)
Attribute: Confidentiality, Integrity
Filled with pride in the harsh Russian hackers, you can go to the service, and register .
This is anonymous, and after submitting the report you will receive information on whether similar cases have occurred, how to solve this problem safely or to avoid its occurrence in the future.
Source: https://habr.com/ru/post/108019/
All Articles