Cross-platform malware: Linux, MacOS, Windows
Given the recent controversy and the requirements to show the virus not under Windows , I allow myself a small translation of an interesting blog by Jerome Segura, a security specialist from ParetoLogic .
The Koobface worm once again falls into the news in its multiplatform version. Intego, a computer security company, discovered a version of this worm on Mac OS X systems and reported it on its blog .
Does the worm enter the victim’s computer through an infected web page of the following type? The following image shows the infection process under Ubuntu:
')

The worm uses a Java applet to download malicious content. If the user agrees to run the applet, his system will become part of the botnet.
The described mechanism was checked by me on Windows, Linux and OS X operating systems. Thus, on Ubuntu, after closing Firefox, traffic continued to be generated:
At the same time, it is interesting that in order to infect the system, it was not necessary to enter the administrator password; it is enough just to run the applet.
Some additional information about the site that distributes this version of Koobface - in case of a successful infection, a random image is displayed:

If you refresh your browser window, a new picture will be displayed each time. The authors of Koobface hotornot.com and display pictures from it:

If the infection fails, you will see the following:

As it turned out, the malicious Java applet is named jnana.tsa. You can see its implementation in the following image:
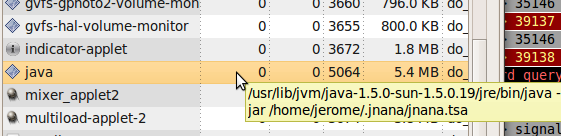
The applet loads the content into the current user's Home directory, and then sends it to be executed:

The Koobface worm remains active for the duration of the java-process activity. However, after a restart, the auto-start of the malware will not occur, except in the case of infection of systems running Windows, where the malware is registered to run in the registry. Having no such possibility under Ubuntu, the worm is active until the system is rebooted, which can be several hours or even days.
UPD: Kaspersky analysts also took up the worm . True, they do not believe in the infection of Ubuntu yet.
The Koobface worm once again falls into the news in its multiplatform version. Intego, a computer security company, discovered a version of this worm on Mac OS X systems and reported it on its blog .
Does the worm enter the victim’s computer through an infected web page of the following type? The following image shows the infection process under Ubuntu:
')

The worm uses a Java applet to download malicious content. If the user agrees to run the applet, his system will become part of the botnet.
The described mechanism was checked by me on Windows, Linux and OS X operating systems. Thus, on Ubuntu, after closing Firefox, traffic continued to be generated:
At the same time, it is interesting that in order to infect the system, it was not necessary to enter the administrator password; it is enough just to run the applet.
Some additional information about the site that distributes this version of Koobface - in case of a successful infection, a random image is displayed:

If you refresh your browser window, a new picture will be displayed each time. The authors of Koobface hotornot.com and display pictures from it:

If the infection fails, you will see the following:

As it turned out, the malicious Java applet is named jnana.tsa. You can see its implementation in the following image:

The applet loads the content into the current user's Home directory, and then sends it to be executed:

The Koobface worm remains active for the duration of the java-process activity. However, after a restart, the auto-start of the malware will not occur, except in the case of infection of systems running Windows, where the malware is registered to run in the registry. Having no such possibility under Ubuntu, the worm is active until the system is rebooted, which can be several hours or even days.
UPD: Kaspersky analysts also took up the worm . True, they do not believe in the infection of Ubuntu yet.
Source: https://habr.com/ru/post/107211/
All Articles