Personal data of conference participants in complete safety
 See the picture on the left, or how I participated in CityCamp , even without going to St. Petersburg.
See the picture on the left, or how I participated in CityCamp , even without going to St. Petersburg.And if not joking, I’ll tell you how it took me a simple honest programmer just a couple of minutes of free time to get access to personal data (email addresses, information about work place and position, cell phone numbers, etc.) of CityCamp conference participants and 11 others .
Caution traffic.
Prehistory
Late Saturday evening, before going to bed, Gruznov and I decided to discuss some of the cases on Skype, and besides, I wanted him to tell me about the cityscape, which he visited during the day. In addition, the conversation turned to the developers with whom he met at the conference, and their startup. And their activity consists in creating a system for deploying Internet resources for events like a citycamp.')
Having received the link and 4-letter-digital access code from his account, I was able to see what their system is. In general, this is something like a mini-contact for conference participants and everything is pretty dull. The icons are clearly from free stocks, the interface does not shine, a full and persistent feeling of "assembling on the knee." Looking ahead, I would say that no matter how it seemed at first glance, a whole team of developers worked on this project, it seems that they even have their own office. This is not a schoolboy you did! Although some students would probably do better. In general, good fun ... =)
Closer to the point
First of all, like any curious developer, I wanted to know what it was done with. Mikhail unfortunately did not have such information, so I first looked at the headers of the web server's response (you never know) and looked in html:
Wow, 17 tsesesok ... =) Well, let's say it is excusable for beta. It also turned out that the center tag is again in fashion, writing at least some short html 5 doctyp is not fashionable, and you can write <style> bla-bla </ style> directly into body. On directives, which, in theory, should be in the headers of the web server, but turned out to be in html in the browser, and the rest of the horrors, so close my eyes.
Then I suddenly wanted to look at the 404 error and I, having entered the habrokadabru in the address bar of the browser, turned out to be ... where would you think? For some reason, on the login page with which I started:

Then something just started to shake and twitch eyes. This is not just an activation code! What I initially did not pay attention to. All conference participants log into their accounts with the help of four letters with dials.
Feint ears
Immediately, I found that the case of letters does not matter. I did not even hope to have any protection for the login frequency and the counter of unsuccessful attempts. And this was not. I shared my thoughts with Michael and we quickly estimated the number of possible combinations and the roughly maximal time of the most primitive http-brute-force to their full brute force. They laughed, and decided that tomorrow Mikhail would have a good excuse for a report, and I would vividly demonstrate that no one was in danger.Then I opened firebug, but something started to get buggy with me after the update, then I just looked at the form code and realized that probably our friends not only couldn’t make up, but didn’t distinguish get from post. Although the form sent post requests, however, the address of the form myrange.ru/login?code=fuck was also a success.
We agreed that at night I will receive the entire list of logins and in the morning I will drop him a report. Wishing good night got down to business. Everything was crazy and trivial. In case of successful authentication, the server returned the 302nd redirect to the profile page, otherwise the 200th code with the login form.
I opened the editor, and lightly curled mana on the curl after a minute, the result:
#!/bin/bash for w in {{a..z},{0..9}}{{a..z},{0..9}}{{a..z},{0..9}}{{a..z},{0..9}}; do curl -I --write-out %{http_code} --silent --output /dev/null http://myrange.ru/login?code=$w; echo " $w"; done saved as brute.sh, and then launched (setting the executable flag in this case would be superfluous, and the home section is mounted with noexec):$ sh brut.sh > brut.txtIt was possible to observe:
$ tail -f brut.txthow quickly the records of the form crawled:
...
200 abc0
200 abc1
302 abc2
200 abc3
...
The first 5 logins were received in a minute. Further, this number is growing rapidly.
$ grep 302 brut.txt | wc -l
336A sample check showed that everything works:
and I'm adding the volume to the speakers and turning on the admin clock
$ sleep 5h && cat /dev/urandom >> /dev/dspwent to sleep.
I woke up after the Skype call, Michael got up earlier. I was surprised to find that brutal had not yet come to an end. The reason for this was immediately revealed. After ~ 200,000 head requests to their server for more than 5 hours (only 10 per second), their entire site began to work at a snail's pace. I stopped the brute, but the situation did not improve, another half an hour probably the pages opened for several minutes, then the situation slowly began to improve, but finally it did not get better.
I then tried it for the sake of experiment and brute went like this: 10 requests quickly, then a 4-5 second pause, three quickly, and a 4-5 pause, then repeated. Whether the admin on the server did something, but it is unlikely, it is not clear, if he watched at least the logs, then why didn’t he immediately ban my aypishnik, stopping the ugliness? Either ... so again I wondered what it was working on. They obviously have somewhere there is a memory leak or open connections, something like that.
Results
There was no point to continue brutating further, Mikhail was about to leave, and I quickly threw him what happened:$ grep 302 brut.txt | cut -d ' ' -f2 > brut.sep.txtI also expressed a desire to write an article on Habr, perhaps for someone else this will be a lesson. We agreed that he would tell the developers to turn off all the nafig and let me know. Then I can post it.
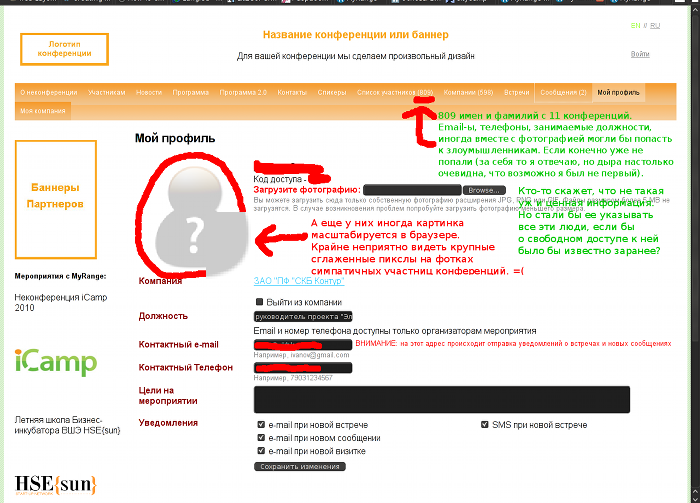
But I never allowed my main curiosity, and therefore I wanted to walk around the site a little more. But they are going to sell it:
Happiness and satisfaction came quickly, completely unexpectedly, at some banal operation (switching from profile to a list of participants) received:
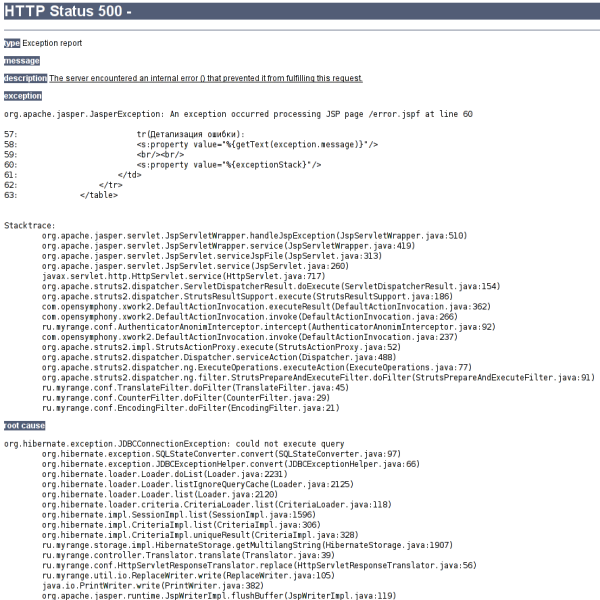
I did not have time to rejoice, as the next step I received:
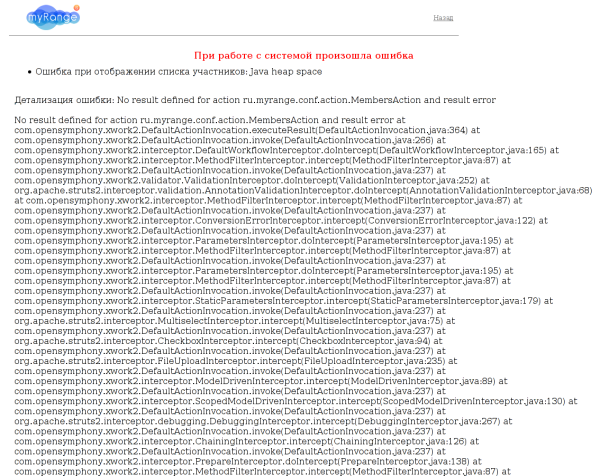
You guys are not ohreneli? This production is already working in real life on real users, what the hell is the traces? There, as I understand it, you have a team of at least four people (sorry if I am mistaken), but didn’t it even occur to your designer that a four-character access code is a go-open? I do not know how you will get out now, perhaps you will put at least a trivial captcha? It’s so simple, a few minutes of competent coder time, there are ready-made solutions. No protection, but at least this post would not exist. I am not a hacker (in the Russian sense of the word), a simple programmer. If writing a brute-script required captcha recognition and took longer than a couple of minutes, I would not spend on this nonsense of my time. Although, I am afraid the general situation is as follows, and if I had a closer look, I would have found a number of through holes.
But all this is simply not in any gate intermeddle. I even collect Gentoo with Hardened patches for projects, and here it is. This is the basics! What, what, innovations, conferences, startups? And this is not a beta, this is some kind of early alpha, I would even say, this is a prototype.
Draw your own conclusions.
ps This morning, after the opening of the campaign, all interested parties were informed and warned. It took several hours. I was given the go-ahead to post, and it seems that they are not going to turn off this login form at all, they say so, but let it be so.
pps From the beginning to the end you are dealing with a piece of art. The events described in it may have only partial similarities with reality, which is accidental. And the persons mentioned are fictional heroes, any coincidences with real people are nothing more than an accident. The narration is conducted on behalf of a third person.
UPD: Reaction followed . Well, the answer is decent, nice. Sorry for the excessive sarcasm and ridicule in the topic, but I hope it will serve as another lesson for the future.
UPD2: Fixed the problem, access to the site is restored.
Source: https://habr.com/ru/post/106769/
All Articles