Caution - unauthorized traffic!
It is no secret to anyone that when you connect any network device to the Internet, traffic is generated, which we “did not order”. Main sources:
The article does not have step-by-step instructions for network security. Hopefully, the users will make the material reflect, and experienced network administrators will add concrete information.
The article does not contain references and GMOs.
Uncontrolled network activity. Even if your connection is 100% closed - if you have a real fixed IP address and not a gray and / or dynamic IP address provided by your ISP for the internal network - broadcast, ICMP, keepalive packets and various service are transferred from the Internet traffic. In this case, anyone can contact your IP address using the simplest
Moreover, even if your network equipment is turned off, traffic can be generated and taken into account by the ISP - until the provider’s ARP cache (which keeps the correspondence between IP and MAC addresses) is removed. The update time depends on the settings at the provider, usually several minutes (in Cisco routers - by default 4 hours).
If kl. the attacker does not set himself the goal of attacking your IP address - this traffic represents several KB per day, but it is not possible to avoid it. Of course, Internet providers usually take the necessary measures to protect.
')
Modern software installed on your computer, often without explicitly asking for your permission, refers to external services to transmit service information, request updates and download them. Those. This traffic is not a necessary part of the program. For example, Adobe, Microsoft, etc. software accesses the Internet to check for updates and registration information. And the Microsoft OS also downloads updates by default, which can exceed hundreds of MB in size.
The way out of this situation can be to disable updates and access to external resources in the software settings (not always possible) and install a software firewall (firewall), which, with all requests for accessing external resources, will ask for your solution. The "learning mode" is present in most modern firewalls.
It occurs due to infection of your computer with viruses. This is the worst option of the above, because in addition to creating parasitic traffic, an attacker can gain access to your computer - with all the ensuing consequences.
The solution is to install antiviruses and regularly update the operating system and software. Moreover, this applies not only to Windows-based systems. Vulnerabilities are detected with enviable regularity in all operating systems, and no one has canceled the check for rootkits. There is specialized software that tracks the detection of vulnerabilities and informs about the availability of updates for common software. For example, for Windows systems, there is Secunia Personal Software Inspector. For Linux systems, if the software was installed from the official repositories, the same tasks are performed by the Package Managers.
With a low level of security, this is typical for the local networks of the enterprise. And with the spread of WiFi-devices - and for ordinary users. Very often, users do not care about the security of wireless connections and open (or insufficiently protected) access points can detect a significant amount - only from my balcony you can “see” two. I must caution that when connected to an open access point - its owner can scan traffic for the presence of clear logins and access passwords.
If everything is clear with the local networks of enterprises - you need to hire qualified system administrators, then owners of home access points are strongly advised to read the documentation to ensure maximum security. There are many informative articles on this topic.
The following logs became a frank surprise for me (calls to Google addresses less than 5MB were excluded from logs):
Those. Every half an hour, within a few days, about 6MB passes from the addresses of Google when the computer is locked. Enough to run Google Chrome. Unfortunately, I haven’t yet figured out the goals of this traffic.
Of course, there is a cardinal solution - unlimited tariffs. But be careful,% username%, monitor traffic and check logs. You never know ...
Of course, for all unauthorized traffic to your IP address, you will have to pay. I can see that on demand most providers provide detailed traffic details without any problems. There are cases when Internet providers go to meet customers and adjust traffic. Especially, it concerns legal entities.
Thanks in advance for your comments and questions.
UPD
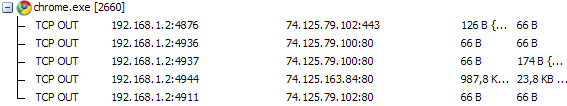
This situation is observed even if one empty tab is open. Google Chrome 6.0.472.63 (the browser happily informs you that this is the latest version).
- Parasitic traffic;
- Unwanted traffic from software;
- Viral activity;
- Unauthorized use of the connection.
The article does not have step-by-step instructions for network security. Hopefully, the users will make the material reflect, and experienced network administrators will add concrete information.
The article does not contain references and GMOs.
Parasitic traffic
Uncontrolled network activity. Even if your connection is 100% closed - if you have a real fixed IP address and not a gray and / or dynamic IP address provided by your ISP for the internal network - broadcast, ICMP, keepalive packets and various service are transferred from the Internet traffic. In this case, anyone can contact your IP address using the simplest
ping ... , a vulnerability ping ... , or try to disrupt the connection by generating the syn flood command hping3 command (for Linux systems). In this case, incoming traffic is generated and taken into account.Moreover, even if your network equipment is turned off, traffic can be generated and taken into account by the ISP - until the provider’s ARP cache (which keeps the correspondence between IP and MAC addresses) is removed. The update time depends on the settings at the provider, usually several minutes (in Cisco routers - by default 4 hours).
If kl. the attacker does not set himself the goal of attacking your IP address - this traffic represents several KB per day, but it is not possible to avoid it. Of course, Internet providers usually take the necessary measures to protect.
')
Traffic from software
Modern software installed on your computer, often without explicitly asking for your permission, refers to external services to transmit service information, request updates and download them. Those. This traffic is not a necessary part of the program. For example, Adobe, Microsoft, etc. software accesses the Internet to check for updates and registration information. And the Microsoft OS also downloads updates by default, which can exceed hundreds of MB in size.
The way out of this situation can be to disable updates and access to external resources in the software settings (not always possible) and install a software firewall (firewall), which, with all requests for accessing external resources, will ask for your solution. The "learning mode" is present in most modern firewalls.
Viral activity
It occurs due to infection of your computer with viruses. This is the worst option of the above, because in addition to creating parasitic traffic, an attacker can gain access to your computer - with all the ensuing consequences.
The solution is to install antiviruses and regularly update the operating system and software. Moreover, this applies not only to Windows-based systems. Vulnerabilities are detected with enviable regularity in all operating systems, and no one has canceled the check for rootkits. There is specialized software that tracks the detection of vulnerabilities and informs about the availability of updates for common software. For example, for Windows systems, there is Secunia Personal Software Inspector. For Linux systems, if the software was installed from the official repositories, the same tasks are performed by the Package Managers.
Unauthorized use of the connection
With a low level of security, this is typical for the local networks of the enterprise. And with the spread of WiFi-devices - and for ordinary users. Very often, users do not care about the security of wireless connections and open (or insufficiently protected) access points can detect a significant amount - only from my balcony you can “see” two. I must caution that when connected to an open access point - its owner can scan traffic for the presence of clear logins and access passwords.
If everything is clear with the local networks of enterprises - you need to hire qualified system administrators, then owners of home access points are strongly advised to read the documentation to ensure maximum security. There are many informative articles on this topic.
And google?
The following logs became a frank surprise for me (calls to Google addresses less than 5MB were excluded from logs):
IP
...
00:10 74.125.160.81 6,059,987 140,082
00:40 74.125.163.83 5,947,266 137,562
01:20 74.125.173.17 5,945,612 136,087
02:10 74.125.173.23 5,948,572 141,739
02:50 74.125.173.21 5,954,547 136,007
03:20 74.125.173.29 5,956,884 135,779
03:50 74.125.173.30 5,958,999 135,807
04:20 74.125.173.23 5,984,194 140,108
04:50 74.125.173.19 5,980,806 140,027
...
Those. Every half an hour, within a few days, about 6MB passes from the addresses of Google when the computer is locked. Enough to run Google Chrome. Unfortunately, I haven’t yet figured out the goals of this traffic.
Of course, there is a cardinal solution - unlimited tariffs. But be careful,% username%, monitor traffic and check logs. You never know ...
Of course, for all unauthorized traffic to your IP address, you will have to pay. I can see that on demand most providers provide detailed traffic details without any problems. There are cases when Internet providers go to meet customers and adjust traffic. Especially, it concerns legal entities.
Thanks in advance for your comments and questions.
UPD

This situation is observed even if one empty tab is open. Google Chrome 6.0.472.63 (the browser happily informs you that this is the latest version).
Source: https://habr.com/ru/post/106061/
All Articles