Stuxnet. Hysteria continues ...
The topic of the Stuxnet worm on Habré has already been discussed many times. It would seem that they covered the event from all sides, but still many important moments remained behind the scenes. The fact is that behind all this “yellowish” information noise that is now appearing in the media, the essence is not visible. But until now, no one can answer exactly the question why and to whom such an attack could be beneficial. There is no one who has direct facts, and only conjectures made on a rather shaky foundation of circumstantial evidence appear. But let's talk about everything in order.
At the conference VB'2010 , which was held in Vancouver last week, they talked a lot about this attack, and from different angles. The most interesting on this topic was the performance of “An indepth look into Stuxnet” from a researcher from Symantec, Liam O'Murchu. As part of his report, a curious demonstration was held, which showed the result of the operation of the SCADA system.
')
What is the purpose of the Stuxnet attack? No one can answer this question so far, because, despite all the statistical indicators, it is not clear which object could have been the real target of the attackers, and perhaps there were several of these goals, or the task was to hit as many objects using the system as possible. SCADA from Siemens. When discussing the functionality of Win32 / Stuxnet, consider the following factors:
- Availability of functionality that allows it to send system parameters of interest to attackers to a remote server;
- Ability to update yourself and expand its functionality from a remote server.
Given these facts, the targets of the attackers could vary, both from each particular system affected by the worm, and depending on the time period of the attack. Such conclusions greatly complicate the search for the true motives of the creators of Win32 / Stuxnet. It is also worth considering that this worm attracted attention only at the end of June 2010. But there is information indicating that this attack has already been developed for a long time (about a year). For example, Symantec specialists discovered a copy of a worm, dated June 2009, moreover, in its capabilities it is more modest.
Now let's turn to statistics. To date, the most saturated region, in terms of the number of incidents, are Asian countries. According to our statistics, the distribution from the beginning of detection to the end of September is as follows:
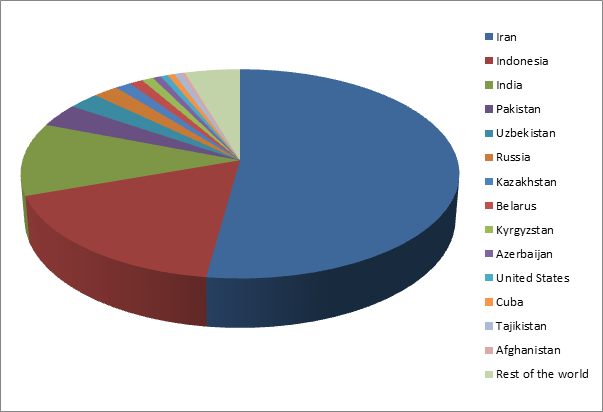
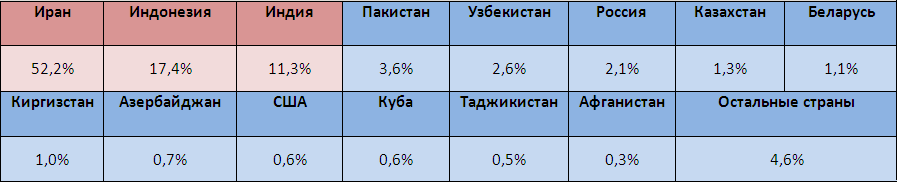
Statistics of other anti-virus companies also indicate that Iran is the most active zone. It is worth, of course, to take into account that all these data are made only on the basis of the number of workstations with an anti-virus product installed. But, nevertheless, the statistical sampling was done for a sufficiently long time period, which reduces the possibility of error.
Based on these data, some are trying to conclude that Iran is the main goal of virus writers. In fact, this data does not say anything about goals. But according to the numbers, it can be assumed that, perhaps, the first copies of the worm were activated in Asia, and the fraudsters could not control the number of infections. The fact is that in the latest version of Win32 / Stuxnet, the functionality is already available that allows you to control the number of infections. Maybe it was this version that was distributed in other regions, which allowed attackers to start controlling its distribution.
And finally, I want to speculate on the cost of this kind of attack, and who could be behind all this. The Win32 / Stuxnet malware is implemented at a high technical level, in many cases with knowledge of how modern defenses are costing. A carefully thought-out object-oriented architecture, a modular system and a large amount of code allow us to conclude that a whole group of professionals (approximately 5-7 people) worked on this development. The zero-day vulnerability MS10-046 was used as the main propagation mechanism. This vulnerability in LNK / PIF files allows to execute arbitrary code. Used by the worm to spread through external media.
Also, the second echelon of vulnerabilities was present, which was exploited when it was already distributed within the local network segment:
- MS10-061 - vulnerability in the Print Spooler service that allows you to execute remotely arbitrary code;
- MS08-067 - a vulnerability in RPC, which has long been closed and used for its spread by the Conficker worm. In this case, this propagation vector was used as an additional;
- (missing Vendor-ID) vulnerability in win32k.sys, which allows to increase local privileges on Win2000 / WinXP systems. Used by the worm with insufficient privileges in the installation process.
- (missing Vendor-ID) vulnerability in Task Scheduler, which allows to increase local privileges on Vista / Win7 systems.
Both of these unclosed vulnerabilities have already begun to appear on the market and are likely to become widespread in the near future. Now there are no official bulletins for these vulnerabilities, nor official information about when they will be closed.
Another interesting zero-day vulnerability is CVE-2010-2772 . This time it was found in Siemens Simatic WinCC and PCS 7 SCADA systems. It consists of a hard-coded password for accessing the Microsoft SQL database from the WinCC program.
Considering all this, only the cost of the technical implementation of Win32 / Stuxnet reaches an amount in excess of 500.000 Euro. This is a very large investment, and, given the fact that this malware does not have a direct monetization scheme, most likely, malicious software was created by some influential or governmental organization. The true motives and goals of creating Win32 / Stuxnet can only be revealed by the authors of this attack themselves, but, apparently, nobody will catch them.
Now the main sources of technical information on the Win32 / Stuxnet worm are two research reports:
Stuxnet Under the Microscope , ESET;
W32.Stuxnet Dossier , Symantec.
At the conference VB'2010 , which was held in Vancouver last week, they talked a lot about this attack, and from different angles. The most interesting on this topic was the performance of “An indepth look into Stuxnet” from a researcher from Symantec, Liam O'Murchu. As part of his report, a curious demonstration was held, which showed the result of the operation of the SCADA system.
')
What is the purpose of the Stuxnet attack? No one can answer this question so far, because, despite all the statistical indicators, it is not clear which object could have been the real target of the attackers, and perhaps there were several of these goals, or the task was to hit as many objects using the system as possible. SCADA from Siemens. When discussing the functionality of Win32 / Stuxnet, consider the following factors:
- Availability of functionality that allows it to send system parameters of interest to attackers to a remote server;
- Ability to update yourself and expand its functionality from a remote server.
Given these facts, the targets of the attackers could vary, both from each particular system affected by the worm, and depending on the time period of the attack. Such conclusions greatly complicate the search for the true motives of the creators of Win32 / Stuxnet. It is also worth considering that this worm attracted attention only at the end of June 2010. But there is information indicating that this attack has already been developed for a long time (about a year). For example, Symantec specialists discovered a copy of a worm, dated June 2009, moreover, in its capabilities it is more modest.
Now let's turn to statistics. To date, the most saturated region, in terms of the number of incidents, are Asian countries. According to our statistics, the distribution from the beginning of detection to the end of September is as follows:


Statistics of other anti-virus companies also indicate that Iran is the most active zone. It is worth, of course, to take into account that all these data are made only on the basis of the number of workstations with an anti-virus product installed. But, nevertheless, the statistical sampling was done for a sufficiently long time period, which reduces the possibility of error.
Based on these data, some are trying to conclude that Iran is the main goal of virus writers. In fact, this data does not say anything about goals. But according to the numbers, it can be assumed that, perhaps, the first copies of the worm were activated in Asia, and the fraudsters could not control the number of infections. The fact is that in the latest version of Win32 / Stuxnet, the functionality is already available that allows you to control the number of infections. Maybe it was this version that was distributed in other regions, which allowed attackers to start controlling its distribution.
And finally, I want to speculate on the cost of this kind of attack, and who could be behind all this. The Win32 / Stuxnet malware is implemented at a high technical level, in many cases with knowledge of how modern defenses are costing. A carefully thought-out object-oriented architecture, a modular system and a large amount of code allow us to conclude that a whole group of professionals (approximately 5-7 people) worked on this development. The zero-day vulnerability MS10-046 was used as the main propagation mechanism. This vulnerability in LNK / PIF files allows to execute arbitrary code. Used by the worm to spread through external media.
Also, the second echelon of vulnerabilities was present, which was exploited when it was already distributed within the local network segment:
- MS10-061 - vulnerability in the Print Spooler service that allows you to execute remotely arbitrary code;
- MS08-067 - a vulnerability in RPC, which has long been closed and used for its spread by the Conficker worm. In this case, this propagation vector was used as an additional;
- (missing Vendor-ID) vulnerability in win32k.sys, which allows to increase local privileges on Win2000 / WinXP systems. Used by the worm with insufficient privileges in the installation process.
- (missing Vendor-ID) vulnerability in Task Scheduler, which allows to increase local privileges on Vista / Win7 systems.
Both of these unclosed vulnerabilities have already begun to appear on the market and are likely to become widespread in the near future. Now there are no official bulletins for these vulnerabilities, nor official information about when they will be closed.
Another interesting zero-day vulnerability is CVE-2010-2772 . This time it was found in Siemens Simatic WinCC and PCS 7 SCADA systems. It consists of a hard-coded password for accessing the Microsoft SQL database from the WinCC program.
Considering all this, only the cost of the technical implementation of Win32 / Stuxnet reaches an amount in excess of 500.000 Euro. This is a very large investment, and, given the fact that this malware does not have a direct monetization scheme, most likely, malicious software was created by some influential or governmental organization. The true motives and goals of creating Win32 / Stuxnet can only be revealed by the authors of this attack themselves, but, apparently, nobody will catch them.
Now the main sources of technical information on the Win32 / Stuxnet worm are two research reports:
Stuxnet Under the Microscope , ESET;
W32.Stuxnet Dossier , Symantec.
Source: https://habr.com/ru/post/105507/
All Articles