Reputation technologies to combat the growing number of threats
Today, almost any sufficiently purposeful schoolchild can launch his “own” Trojan, and for this he does not need to have knowledge of programming, does not need to be an expert in finding vulnerabilities, does not need to be able to carry out mass infections through spam emails or hacking sites - all this can be done compensate for a couple of hundred dollars saved on breakfast. A whole market of underground services was formed, where you can buy designers for creating phishing sites and Trojans, order infecting a certain number of ordinary people, and sell the results of your own Trojan - logins and passwords, credit card numbers - to sell to the following links in the criminal chain. Our hypothetical schoolboy presses a button in the constructor, and now the standard malicious code is modified into a new, yet unknown antivirus. It is because of the simplification of the process of creating and distributing the number of unique malware samples that are constantly growing, anti-virus companies are trying to compensate for this with constant signature updates, but in fact they are always behind the threat, because the signature method is inherently reactive.

There is a way out of the race, and it is based on an understanding of the nature of modern threats and on the principles of reputation. In the process of infecting a Trojan and other malware, communicating with the control center and sending the collected data, the victim’s machine’s contact with specific servers under the attacker's control. It is at this point that you can prevent infection or block the sending of the collected data to the drop zone, simply by not allowing the network interaction to take place.
')
With the constant increase in the number of malware samples, it is necessary to combine reactive and proactive protection methods - the signature approach alone is not enough. Even if antivirus companies are now trying to release updates every few minutes, in the future it will be almost impossible to keep up with the exponential growth in the number of threats. If the constant work of analyzing the code and updating the signatures protects against known threats, then reputation technologies allow you to avoid infecting with new malware by stopping communications with well-known servers with a “bad” reputation.
Denis Bezkorovayny
technical consultant Trend Micro

There is a way out of the race, and it is based on an understanding of the nature of modern threats and on the principles of reputation. In the process of infecting a Trojan and other malware, communicating with the control center and sending the collected data, the victim’s machine’s contact with specific servers under the attacker's control. It is at this point that you can prevent infection or block the sending of the collected data to the drop zone, simply by not allowing the network interaction to take place.
')
How to determine which server is dangerous?
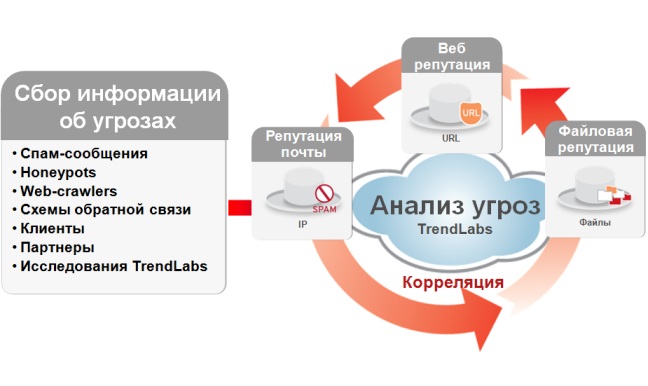
This requires a constantly available, fault-tolerant database containing information about the addresses of malicious servers - servers hosting phishing websites, installers of Trojans and bots containing bot net control centers and their drop zones. When requesting all network connections, the security system must intercept them and check the reputation of addresses, that is, find out whether the address of the requested server is on the “black list” and, if so, block communication with this server.How to ensure the relevance of data in the URL reputation database?
Ideally, such a database should contain information about all URLs and servers, both malicious and “clean”. The following sources can be used to populate the database with addresses of malicious servers:- Spam e-mails that lure users to phishing sites and sites with malware uploaders;
- Automatic analyzers - crawlers that scan the network for known viruses;
- Malware code analysis - allows you to identify addresses of management servers, updates and drop-zones;
- Feedback schemes embedded in anti-virus products - they provide previously unknown links for analysis and categorization;
- Honeypots - network traps to collect fresh current attacks and threats;
- External data from information security vendors.
Implementation
The approach described above was implemented by Trend Micro, the URL reputation database is part of a set of technologies under the common name Smart Protection Network. In addition to the URL reputation database, Smart Protection Network includes a file reputation database and an email reputation database containing information about known spam senders. This allows you to correlate data from three databases, for example, when analyzing spam emails, the sender's address (this can also be one of the botnet members) is entered into the reputation reputation database, the link leading to the Trojan downloader goes into the web reputation database as malicious, and the executable file of the loader gets into the database of file reputation.
What does this give a simple user?
All Trend Micro products — for home users and corporate customers — use URL reputation queries when contacting any application on the protected machine, including a browser, with the Internet.Why is it effective?
As a rule, the same servers are involved in many criminal projects - on one server there can be a botnet control center and dozens of domains for phishing attacks. Thus, once the "lit" server will be blocked in all subsequent attacks.With the constant increase in the number of malware samples, it is necessary to combine reactive and proactive protection methods - the signature approach alone is not enough. Even if antivirus companies are now trying to release updates every few minutes, in the future it will be almost impossible to keep up with the exponential growth in the number of threats. If the constant work of analyzing the code and updating the signatures protects against known threats, then reputation technologies allow you to avoid infecting with new malware by stopping communications with well-known servers with a “bad” reputation.
Denis Bezkorovayny
technical consultant Trend Micro
Source: https://habr.com/ru/post/105234/
All Articles