How many holes in Adobe caftan? (CVE-2010-2883)
According to the number of exploited vulnerabilities, Adobe Acrobat Reader is one of the most “worn” and, at the same time, the most popular among attackers. Attacks using vulnerabilities in Adobe applications for client-side attacks have long been a trend. Last time we wrote about loud 0-day vulnerabilities in the summer . Recently, attackers have a new reason for creativity.
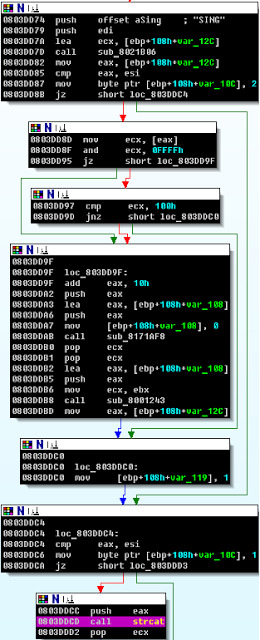
On Thursday, another 0-day for Adobe Reader ( CVE-2010-2883 ) was made public. This time, the CoolType.dll library, which is responsible for the True Type Font parsing, turned out to be guilty. Vulnerability manifests itself when processing a font with an incorrect SING table . During processing, an insecure sishcat strcat () function is called , which, under certain conditions, leads to a stack overflow.
')
The first person to notice the malicious JS / Exploit.Pdfka.OFZ (9c5cd8f4a5988acae6c2e2dce563446a) that exploited this vulnerability was Mila Parkour . Thanks to her efforts, the right people paid attention to JS / Exploit.Pdfka.OFZ and figured out what was wrong.
And the sample turned out to be really interesting and, apparently, since the end of August it has already been, what is called, ITW. It's not clear why Adobe still uses insecure features. Apparently, the company was counting on the options of the compiler / GS and / SAFESEH , with which the CoolType.dll library was compiled. To bypass all these troubles associated with DEP, and other SAFESEH, the ROP technique is used, but to get around ASLR, the icucnv36.dl module was found, also by Adobe authorship and not compiled with the / DYNAMICBASE option. It is in this module that we get when performing a ROP chain placed in memory through a heap-spray attack:
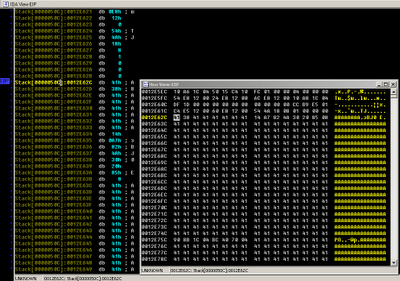
Further, the WinAPI call chain of functions used by the malware is used.
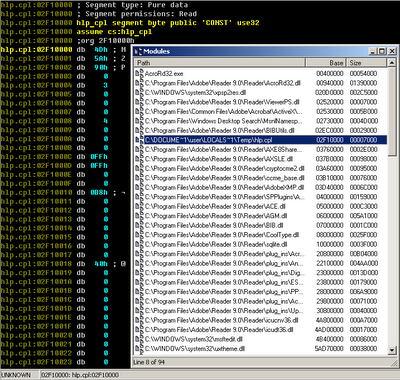
Interestingly, the executable file (“Win32 / TrojanDownloader.Small.OZS”) “dropped” from a pdf-file has a legal digital signature:
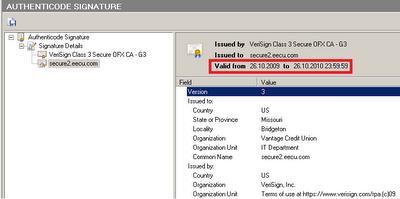
The certificate is valid until the end of October and, probably, therefore, the attackers decided to use it right now. We have already seen games with signed malware when attacking a Win32 / Stuxnet worm. The “drop” module is a dynamic library disguised as cpl and has the following imported functions:
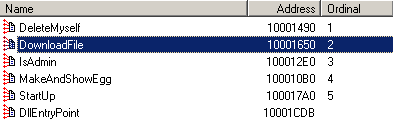
StartUP - downloads from _http: //acad***house.us/from/wincrng.exe and launches this file (Win32 / TrojanDownloader.Small.OZS)
IsAdmin - checks for administrative privileges in the system
DeleteMyself - creates a bat-file that removes this executable from the system
MakeAndShowEgg - restarts Adobe Reader
For this vulnerability, an exploit for Metasploit appeared rather quickly, which also uses heap-spray for ROP placement and subsequent exploitation.
On Thursday, another 0-day for Adobe Reader ( CVE-2010-2883 ) was made public. This time, the CoolType.dll library, which is responsible for the True Type Font parsing, turned out to be guilty. Vulnerability manifests itself when processing a font with an incorrect SING table . During processing, an insecure sishcat strcat () function is called , which, under certain conditions, leads to a stack overflow.

')
The first person to notice the malicious JS / Exploit.Pdfka.OFZ (9c5cd8f4a5988acae6c2e2dce563446a) that exploited this vulnerability was Mila Parkour . Thanks to her efforts, the right people paid attention to JS / Exploit.Pdfka.OFZ and figured out what was wrong.
And the sample turned out to be really interesting and, apparently, since the end of August it has already been, what is called, ITW. It's not clear why Adobe still uses insecure features. Apparently, the company was counting on the options of the compiler / GS and / SAFESEH , with which the CoolType.dll library was compiled. To bypass all these troubles associated with DEP, and other SAFESEH, the ROP technique is used, but to get around ASLR, the icucnv36.dl module was found, also by Adobe authorship and not compiled with the / DYNAMICBASE option. It is in this module that we get when performing a ROP chain placed in memory through a heap-spray attack:

Further, the WinAPI call chain of functions used by the malware is used.

Interestingly, the executable file (“Win32 / TrojanDownloader.Small.OZS”) “dropped” from a pdf-file has a legal digital signature:

The certificate is valid until the end of October and, probably, therefore, the attackers decided to use it right now. We have already seen games with signed malware when attacking a Win32 / Stuxnet worm. The “drop” module is a dynamic library disguised as cpl and has the following imported functions:

StartUP - downloads from _http: //acad***house.us/from/wincrng.exe and launches this file (Win32 / TrojanDownloader.Small.OZS)
IsAdmin - checks for administrative privileges in the system
DeleteMyself - creates a bat-file that removes this executable from the system
MakeAndShowEgg - restarts Adobe Reader
For this vulnerability, an exploit for Metasploit appeared rather quickly, which also uses heap-spray for ROP placement and subsequent exploitation.
Source: https://habr.com/ru/post/104137/
All Articles