IBM X-Force Threat Report: fix numbers
An interesting story occurred with the analytical report of the IBM X-Force Threat Report, which is traditionally published every six months and is devoted to analyzing the latest trends in the field of information security. Among other things, they cite statistics on the number of holes detected (in their database for the first half of 2010 about 4500 vulnerabilities were recorded, by the way, a record number) and on the number of patches. Thus, they make a rating, which vendor copes with the detected vulnerabilities better.
The new report was released last week ( download is allowed after registration, but you can try a direct link to PDF). It is interesting in two things.
First, the document will have to be redone. Authors from IBM have already said that in the coming days they will replace PDF with an FTP server. The problem is that the two companies have protested on the published figures in the ranking of "holey vendors." One of these companies is Google.
In the first version of the report, Google tops the ranking for the worst closure of critical holes with a 33% indicator. But it turned out that this figure was obtained on the basis of only three vulnerabilities revealed in Google services this year, one of which was not closed, and as it turned out later, this was not a bug at all, but the result of terminological confusion .
')
What other company besides Google filed a protest is unknown, but IBM was forced not only to correct the error, but to manually change the data on other vulnerabilities (fixed “critical” status, binding to the vendor, information about the release of patches). Correction of the database was reflected in many indicators.
The old version of the document is preserved on Scribd , so that you yourself can compare the two tables (p. 20).
Table from the old report ...

... will be replaced by a new one.
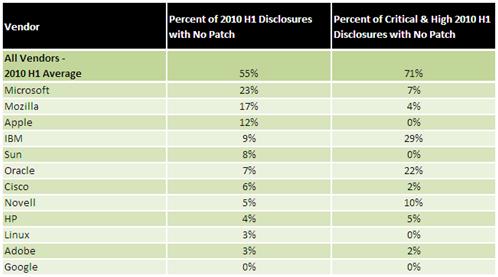
Google's reputation has been cleared and now it’s listed with 0% of unclosed critical holes, as well as Linux and Apple.
As a result, it turned out - and this is the second interesting thing about the report - that after correcting the figures, IBM put itself in the first place in the list of "worst patchers", if we consider only critical vulnerabilities.
The new report was released last week ( download is allowed after registration, but you can try a direct link to PDF). It is interesting in two things.
First, the document will have to be redone. Authors from IBM have already said that in the coming days they will replace PDF with an FTP server. The problem is that the two companies have protested on the published figures in the ranking of "holey vendors." One of these companies is Google.
In the first version of the report, Google tops the ranking for the worst closure of critical holes with a 33% indicator. But it turned out that this figure was obtained on the basis of only three vulnerabilities revealed in Google services this year, one of which was not closed, and as it turned out later, this was not a bug at all, but the result of terminological confusion .
')
What other company besides Google filed a protest is unknown, but IBM was forced not only to correct the error, but to manually change the data on other vulnerabilities (fixed “critical” status, binding to the vendor, information about the release of patches). Correction of the database was reflected in many indicators.
The old version of the document is preserved on Scribd , so that you yourself can compare the two tables (p. 20).
Table from the old report ...

... will be replaced by a new one.

Google's reputation has been cleared and now it’s listed with 0% of unclosed critical holes, as well as Linux and Apple.
As a result, it turned out - and this is the second interesting thing about the report - that after correcting the figures, IBM put itself in the first place in the list of "worst patchers", if we consider only critical vulnerabilities.
Source: https://habr.com/ru/post/103251/
All Articles