TDL4 - the first full-fledged rootkit for x64 systems (Win7, Vista ...)
At the end of last week, a fundamentally new version of the notorious TDL3 rootkit was discovered (there are some facts that suggest that this beast appeared even earlier), the main feature of this version was full support for x64 systems.
TDL4 manages to successfully bypass the protective mechanism for verifying digital signatures in x64 versions of windows-systems. The authors of TDL4 used a rather elegant way of circumventing, which consists of using the MBR infection techniques and launching malicious code before the operating system itself. Such methodologies have already been actively used by such malicious programs as Mebroot , StonedBoot , etc.
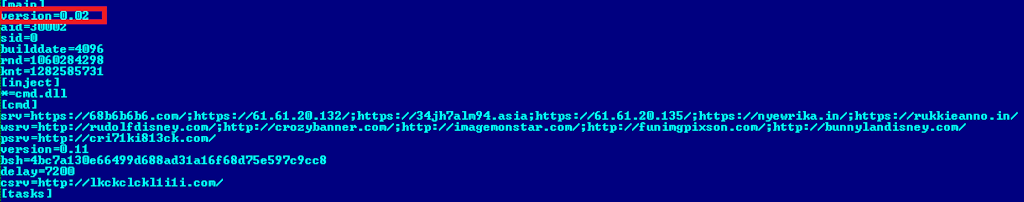
The last common version of the TDL3, which we conducted in the summer of detailed research , was 3.273. Now the revision of versions is carried out from the beginning, and the version considered in the article comes as number 0.02 (the version can be seen in the bot configuration file). Such a strange version number suggests that the authors are only debugging new technologies that appeared in this version, and in the future we will have something more interesting. From the point of view of the functional of fundamental changes, besides the new way of installing the driver through the infection of the MBR and small changes in the hidden file system, we have not noticed. The driver is very similar to what we have already seen in the TDL3 and, most likely, it was just re-assembled taking into account the features of x64 systems. The previous version of the rootkit used a mechanism for infecting system drivers to download the malicious functionality without changing their size, but since the x64 system checks the digital signature when the driver loads, the attackers refused this mechanism.
')
So, now the infection is as follows:
- The handle of the physical device opens (in our case it is \\ ?? \ PhysicalDrive0 ), on which the section named C is located:
- Prepares and records the image of its file system at the end of the hard disk
- Overwrites MBR - code that loads modules in the previously prepared file system
- After successful infection on x64 systems, a reboot occurs by calling the ExitWindowsEx function () .
This is what the decrypted MBR code looks like, and we see the name of the malicious module that will have to be executed in order to launch the rootkit further:

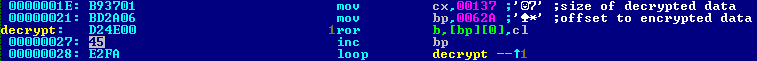
The encryption algorithm is quite simple and comes down to a call in the cycle of the processor command ROR:
The procedure for launching TDL4, taking into account the digital signature verification mechanism bypass:
- Bios reads the first sector of the boot disk and transfers control to the master boot record code of the MBR and thus begins the execution of the TDL4 code
- Next, the code is decrypted for further execution, which is designed to load a module named ldr16 from the rootkit file system
- The loaded module ldr16 intercepts interrupt 13h, which is responsible for working with the hard disk. The main task of this module is to determine the bitness of the operating system (x32 or x64), and depending on it, ldr32 or ldr64 is loaded.
- Both the ldr32 and ldr64 modules are designed to load the main TDL4 driver, which is implemented without using the standard API to bypass the digital signature verification mechanism.
- First, there is a placement of the driver code in the memory to the addresses that represent the kernel of the OS. Then it is registered as an OS driver by calling the undocumented IoCreateDriver () function. After that, the driver can be considered loaded.
Then the loading of the operating system with the TDL4 driver on board continues, after the launch, malicious code is introduced into some processes, and later on its behavior is very similar to the previous version of TDL3. This is what the bot configuration file looks like:
TDL4, like its previous counterparts, fell into the Win32 / Olmarik malware family and is detected by us as a Win32 / Olmarik.ADA rootkit.
TDL4 manages to successfully bypass the protective mechanism for verifying digital signatures in x64 versions of windows-systems. The authors of TDL4 used a rather elegant way of circumventing, which consists of using the MBR infection techniques and launching malicious code before the operating system itself. Such methodologies have already been actively used by such malicious programs as Mebroot , StonedBoot , etc.
The last common version of the TDL3, which we conducted in the summer of detailed research , was 3.273. Now the revision of versions is carried out from the beginning, and the version considered in the article comes as number 0.02 (the version can be seen in the bot configuration file). Such a strange version number suggests that the authors are only debugging new technologies that appeared in this version, and in the future we will have something more interesting. From the point of view of the functional of fundamental changes, besides the new way of installing the driver through the infection of the MBR and small changes in the hidden file system, we have not noticed. The driver is very similar to what we have already seen in the TDL3 and, most likely, it was just re-assembled taking into account the features of x64 systems. The previous version of the rootkit used a mechanism for infecting system drivers to download the malicious functionality without changing their size, but since the x64 system checks the digital signature when the driver loads, the attackers refused this mechanism.
')
So, now the infection is as follows:
- The handle of the physical device opens (in our case it is \\ ?? \ PhysicalDrive0 ), on which the section named C is located:
- Prepares and records the image of its file system at the end of the hard disk
- Overwrites MBR - code that loads modules in the previously prepared file system
- After successful infection on x64 systems, a reboot occurs by calling the ExitWindowsEx function () .
This is what the decrypted MBR code looks like, and we see the name of the malicious module that will have to be executed in order to launch the rootkit further:

The encryption algorithm is quite simple and comes down to a call in the cycle of the processor command ROR:

The procedure for launching TDL4, taking into account the digital signature verification mechanism bypass:
- Bios reads the first sector of the boot disk and transfers control to the master boot record code of the MBR and thus begins the execution of the TDL4 code
- Next, the code is decrypted for further execution, which is designed to load a module named ldr16 from the rootkit file system
- The loaded module ldr16 intercepts interrupt 13h, which is responsible for working with the hard disk. The main task of this module is to determine the bitness of the operating system (x32 or x64), and depending on it, ldr32 or ldr64 is loaded.
- Both the ldr32 and ldr64 modules are designed to load the main TDL4 driver, which is implemented without using the standard API to bypass the digital signature verification mechanism.
- First, there is a placement of the driver code in the memory to the addresses that represent the kernel of the OS. Then it is registered as an OS driver by calling the undocumented IoCreateDriver () function. After that, the driver can be considered loaded.
Then the loading of the operating system with the TDL4 driver on board continues, after the launch, malicious code is introduced into some processes, and later on its behavior is very similar to the previous version of TDL3. This is what the bot configuration file looks like:

TDL4, like its previous counterparts, fell into the Win32 / Olmarik malware family and is detected by us as a Win32 / Olmarik.ADA rootkit.
Source: https://habr.com/ru/post/103249/
All Articles