MakeMeLaughNow - analysis of the worm of a new generation on Facebook (translation)
In a recent topic, they expressed a wish that it would be good if someone translated. I looked at the text - it seems not so much. Therefore, to whom it is interesting, we look ...
New malicious worm application on Facebook is released.
It avoids the “sandbox” mechanism on Facebook and is activated BEFORE, as the authorization form is shown - just by visiting the application page, you start sending a message to your friends and update your status.
According to the news on niebezpiecznik.pl , it uses Facebook mobile site (touch.facebook.com) for distribution. I quickly analyzed - let's see what exactly is in the application code.
')
Disclaimer: Do not do this at home - I am a professional stuntman and besides, I love living dangerously. Do not perform this analysis on your standard Facebook account, use a virtual machine in case an exploit is installed there, and so on. As soon as I found out that the touch.facebook.com site is involved, I added:
in / etc / hosts (it redirects all requests to touch.facebook.com to my computer), but please be careful. You have been warned.
The home page of the application looks like this:
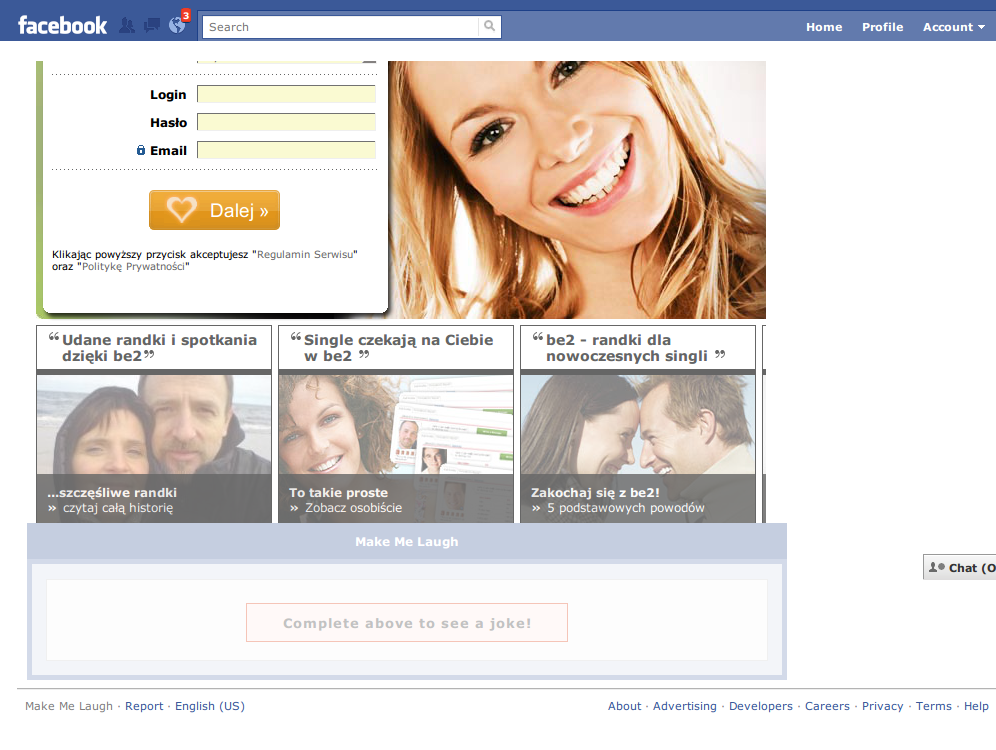
All you can see is a few advertisements. But under this all there is a lot of things. Let's take a look at the Firebug network panel.
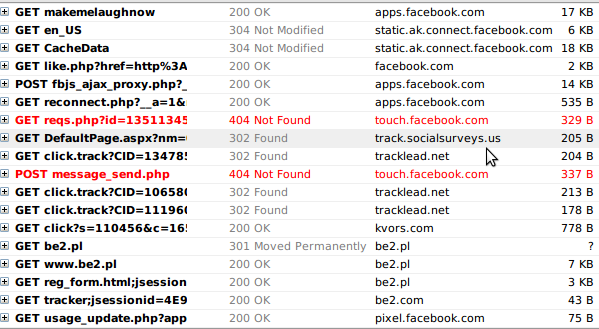
The application, even before requesting any permissions from you, already sends requests to touch.facebook.com, possibly sending messages and performing other actions on your behalf. These requests are marked in red on the screenshot (I blocked the mobile Facebook site). After that, the advertisement is loaded from be2.pl. So the application is definitely malicious.
Get
The code itself and the HTML are in
The code is “jittered” in the JSON file and looks like this: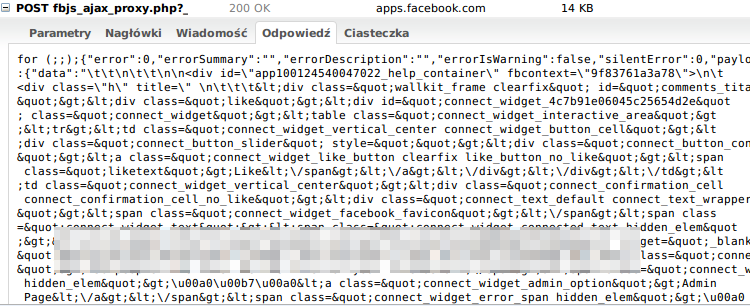
After downloading the JSON file to the local disk and the subsequent extraction (I used PHP & Spidermonkey to extract and Eclipse for formatting) we will get the final application code (see step2_2.js) .
All Facebook applications are “ dirty ” in order to prevent them from referring to the global window object (so that they cannot change the Facebook page, redirect, send hidden forms, and so on). For this particular analysis, the following important points should be noted:
All the code used in this post is hosted on github.com - look, this is really interesting.
After initialization, the application starts with the following ad:
Thus, the application receives the header of one of its DOM elements and passes it to some function. What's in the headline? Looking at the page code ( app.html ), we will see that it looks rather strange:
It looks as if the header is something like a key that can be used to decrypt the hidden variables of the application. And we are right. In fact,
Ok, the application is confusing and uses a DOM object to decrypt its variables. But what does it do?
Let's look at ax_findvalues :
This variable contains quite interesting regular expressions - they are used to extract your friends' IDs, your own IDs, and some unique authenticators from the HTML code embedded in Facebook into the application. But the application can not do anything with this data, as we are protected by "zapochechivaniem", right? Well, not quite.
Hacked by touch is a free translation of the “Exploited by touching” word game, literally meaning that an exploit was used on the mobile site touch.facebook.com. - (approx. Transl.)
Looking deeper into the code, we can see that the jumbled data actually:
So, most likely, the application contacts touch.facebook.com for sending messages and updating statuses. Again, we are right . The process itself:
What we can see here is an application supposedly using a Facebook vulnerability, when the mobile site uses the same authentication as the normal site, but is not protected by the "wrinkling" mechanism. Thus, the application, instead of requesting permission to update your status, quietly receives a session of data from the DOM and sends requests via touch.facebook.com, avoiding sandbox protection and spreading quickly - very similar to the CSRF / session hijacking vulnerability. It’s quite clear that a bug is being used on Facebook. Lesson - do not forget about your mobile sites .
The original is here .
UPD.: As suggested in the comments, the parser korzhit links a bit, so to go through the links, look where they lead and just correct them.
PS If you notice any inaccuracies in the translation - let me know, I do not know Russian programming vocabulary perfectly.
New malicious worm application on Facebook is released.
It avoids the “sandbox” mechanism on Facebook and is activated BEFORE, as the authorization form is shown - just by visiting the application page, you start sending a message to your friends and update your status.
According to the news on niebezpiecznik.pl , it uses Facebook mobile site (touch.facebook.com) for distribution. I quickly analyzed - let's see what exactly is in the application code.
')
Disclaimer: Do not do this at home - I am a professional stuntman and besides, I love living dangerously. Do not perform this analysis on your standard Facebook account, use a virtual machine in case an exploit is installed there, and so on. As soon as I found out that the touch.facebook.com site is involved, I added:
127.0.0.1 touch.facebook.comin / etc / hosts (it redirects all requests to touch.facebook.com to my computer), but please be careful. You have been warned.
Look around quickly
The home page of the application looks like this:

All you can see is a few advertisements. But under this all there is a lot of things. Let's take a look at the Firebug network panel.

The application, even before requesting any permissions from you, already sends requests to touch.facebook.com, possibly sending messages and performing other actions on your behalf. These requests are marked in red on the screenshot (I blocked the mobile Facebook site). After that, the advertisement is loaded from be2.pl. So the application is definitely malicious.
Get shorty code
The code itself and the HTML are in
apps.facebook.com/fbml/fbjs_ajax_proxy.php?__a=1The code is “jittered” in the JSON file and looks like this:

After downloading the JSON file to the local disk and the subsequent extraction (I used PHP & Spidermonkey to extract and Eclipse for formatting) we will get the final application code (see step2_2.js) .
Sandbox
All Facebook applications are “ dirty ” in order to prevent them from referring to the global window object (so that they cannot change the Facebook page, redirect, send hidden forms, and so on). For this particular analysis, the following important points should be noted:
- JS code and objects are in the prefix
aBIGNUMBER_variable_name(aBIGNUMBER_variable_name) - HTML objects have IDs using the
div id="appBIGNUMBER_name"(div id="appBIGNUMBER_name") ( div should be enclosed in triangular brackets, but with them Habrough editor mercilessly korzhet, removed - approx. Transl. ) $FBJSused to prevent the application from linking to the global window object. For our purposes, you can assume that$FBJS.idx(a) === a$FBJS.ref(this) === this- For honors, I replaced BIGNUMBER with the letter 'x'.
All the code used in this post is hosted on github.com - look, this is really interesting.
Analysis
The method of "dullness"
After initialization, the application starts with the following ad:
ax_domethod = ax_findvalues.firefunc(ax_document.getElementById('help_container').getFirstChild().getTitle());Thus, the application receives the header of one of its DOM elements and passes it to some function. What's in the headline? Looking at the page code ( app.html ), we will see that it looks rather strange:
<div id="app100124540047022_m"
class="m"
fbcontext="6ff9e32a4c8c"
title="choy:ketmdslqxb.ujpzgvnra/fiw_?="/>
It looks as if the header is something like a key that can be used to decrypt the hidden variables of the application. And we are right. In fact,
choy:ketmdslqxb.ujpzgvnra/fiw_?= Is a dictionary - the ax_create.help () function picks up characters from this dictionary to form URLs, field names, and so on. Character offsets are defined in the slightly confusing ax_meth variable.Scratching data
Ok, the application is confusing and uses a DOM object to decrypt its variables. But what does it do?
Let's look at ax_findvalues :
var ax_findvalues = {
a : ((new ax_RegExp('st_.or._i.\\\x22 .al.e=\\\x22(.*?)\\\x22', ''))),
// <form action="http://www.facebook.com/wallpost.php" post_form_id value
b : ((new ax_RegExp('b_d.s.\\\x22 v..ue=\\\x22(.*?)\\\x22', ''))),
// value = type="hidden" id="fb_dtsg" name="fb_dtsg"
c : ((new ax_RegExp('po.le\\.pp\\?i.=(\\d+)\\\x22', ''))),
// href="http://www.facebook.com/profile.php?id=xxx" your profile ID
d : ((new ax_RegExp('na.e=\\\x22i.s\\[]\\\x22 vle=\\\x22(.*?)\\\x22', 'gi'))),
// name=ids[] value= -- your friend ids
//...This variable contains quite interesting regular expressions - they are used to extract your friends' IDs, your own IDs, and some unique authenticators from the HTML code embedded in Facebook into the application. But the application can not do anything with this data, as we are protected by "zapochechivaniem", right? Well, not quite.
Hacked by touch
Hacked by touch is a free translation of the “Exploited by touching” word game, literally meaning that an exploit was used on the mobile site touch.facebook.com. - (approx. Transl.)
Looking deeper into the code, we can see that the jumbled data actually:
m=http://touch.facebook.com/message_send.php
ftarg=fra
su=http://touch.facebook.com/submit_status.php (status update)
pid=post_form_id
lp=http://touch.facebook.com/reqs.php?id=
fhome=http://touch.facebook.com/home.php
fbd=fb_dtsg
hc=fb_dtsg
So, most likely, the application contacts touch.facebook.com for sending messages and updating statuses. Again, we are right . The process itself:
- ax_findvalues.firefunc () retrieves your friends' IDs and other data in ax_sheep, ax_params variables ( line 264 )
- Create a new form and iframe
- ax_methodaction ( line 183 ) fills out a form on touch.facebook.com with the following message to some (maximum 20) friends:
i thought of you ...
im using up my fb ad gift to send ua gift so HERE = http: //apps.facebook.com/makemelaughnow/ - If you have more than 500 or less than 2, then the status update: “only go here if you are my TRUE friend http: //apps.facebook.com/makemelaughnow /” (I ’ve got a link that God forbid no one clicked. Habrareditor if it turns off the creation of links, then it turns off automatic hyphenation - approx. transl. ).
- You add yourself this application ( line 297 )
- Advertising is displayed and the application cleans up their objects.
Conclusion
What we can see here is an application supposedly using a Facebook vulnerability, when the mobile site uses the same authentication as the normal site, but is not protected by the "wrinkling" mechanism. Thus, the application, instead of requesting permission to update your status, quietly receives a session of data from the DOM and sends requests via touch.facebook.com, avoiding sandbox protection and spreading quickly - very similar to the CSRF / session hijacking vulnerability. It’s quite clear that a bug is being used on Facebook. Lesson - do not forget about your mobile sites .
The original is here .
UPD.: As suggested in the comments, the parser korzhit links a bit, so to go through the links, look where they lead and just correct them.
PS If you notice any inaccuracies in the translation - let me know, I do not know Russian programming vocabulary perfectly.
Source: https://habr.com/ru/post/103086/
All Articles