"Feature" in IPSEC implementation of Draytek routers VPN
Draytek is a relatively new company in the Russian segment, occupying the niche of low-cost compact routers All-in-one. Here and here you can read a review of the two most popular models of routers of this company of the 2820 and 2910 series (which, by the way, are positioned as a “security firewall”). Among the other advantages of these routers, the most delicious is hardware support for encryption (AES / DES / 3DES) and authentication (MD5, SHA-1), so you can, like, set up VPN between points and sleep peacefully. But not everything is as simple as it seems.
We put together a simple booth - 1 Draytek gateway, 1 VPN server on the front end (connected directly):
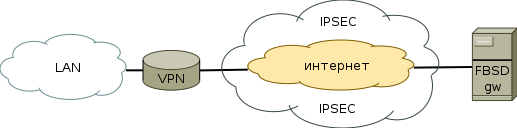
Data
As a server, I took FreeBSD with security / racoon2. We raise VPN, after some time we lower spmd (we disconnect racoon2 on fryakha), we ping the internal address of fryakha (previously having started tcpdump) from Draytek'a. Pinged! Oh hell, how can this be?
Let's model the ideal situation - 2 routers from the manufacturer (2910 and 2820), the gateway in the middle (the same fryah with tcpdump):
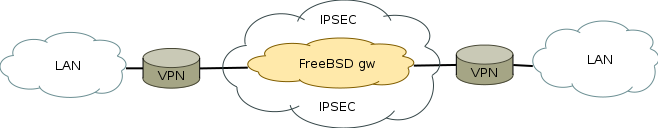
')
Data
3 FreeBSD gw
1 WAN 192.168.51.1
2 WAN 192.168.52.1
sysctl: net.inet.ip.forwarding: 1
When the VPN channel is disconnected (say, the network of the provider has fallen) on router 2, router 1 removes the encrypted tunnel and ... begins to broadcast packet addresses to the external interface!
Draytek Vigor 2910VG and 2820Vn were tested, the behavior is the same. I think all routers of these series are subject to this vulnerability - after a tunnel breaks, the translation of the addresses of outgoing packets begins, which should be encrypted .
Do not look at only ICMP traffic in the video, all IP traffic is broadcast, it can be seen on http packets at the end of the video (laptop for draytek 2910 [ip address 192.168.9.2]).
Manufacturer warned. Correspondence with him:
Here are these feints ears at the expense of standards. And such feints, as you know, do not pass without leaving a trace. IPSEC is a very serious standard that guarantees the security of transmitted information, and here such abug is a feature.
PS I publish it only because I want to warn those who use these routers in production.
We put together a simple booth - 1 Draytek gateway, 1 VPN server on the front end (connected directly):

Data
Draytek 2910:
LAN: 192.168.9.1/24
WAN: 99.99.99.99/24
GW: 99.99.99.100 ()
FreeBSD:
LAN: 192.168.3.32/24
WAN: 99.99.99.100/24As a server, I took FreeBSD with security / racoon2. We raise VPN, after some time we lower spmd (we disconnect racoon2 on fryakha), we ping the internal address of fryakha (previously having started tcpdump) from Draytek'a. Pinged! Oh hell, how can this be?
Let's model the ideal situation - 2 routers from the manufacturer (2910 and 2820), the gateway in the middle (the same fryah with tcpdump):

')
Data
1 Draytek 2910
LAN: 192.168.9.1/24
WAN: 192.168.51.2
GW: 192.168.51.1
2 Draytek 2820
LAN: 192.168.10.1/24
WAN: 192.168.52.2
GW: 192.168.52.13 FreeBSD gw
1 WAN 192.168.51.1
2 WAN 192.168.52.1
sysctl: net.inet.ip.forwarding: 1
When the VPN channel is disconnected (say, the network of the provider has fallen) on router 2, router 1 removes the encrypted tunnel and ... begins to broadcast packet addresses to the external interface!
Draytek Vigor 2910VG and 2820Vn were tested, the behavior is the same. I think all routers of these series are subject to this vulnerability - after a tunnel breaks, the translation of the addresses of outgoing packets begins, which should be encrypted .
Do not look at only ICMP traffic in the video, all IP traffic is broadcast, it can be seen on http packets at the end of the video (laptop for draytek 2910 [ip address 192.168.9.2]).
Manufacturer warned. Correspondence with him:
who support@draytek.com
date August 27, 2010 18:05
bug in your routers theme
I found the bug in your routers (I think this bug in your current xx routers too).
I create test configuration:
192.168.3.0/24 | 192.168.1.10 (freebsd) - 192.168.1.2 (router) | 192.168.9.0/24
I use freebsd os with racoon2 port (ipsec-tools too)
Bug is very serious:
ipod spmd (on freebsd), ipod, ipod, ipod, ipod, ipod, ipod, ipod, ipd All NAT'ed traffic is unencrypted!
You can download video from xxx . I attach router (admin without password) and racoon2 config files.
If you don’t have a lettersome lettersdate September 2, 2010 8:20
Re: [Ticket # 2010082810002448] Fwd: bug in your routers
Dear sir
Thank you for the information.
Although it provides flexibility
for many applications. For example when vpn is up, a public server is accessed
through a vpn tunnel and routed to the Internet by remote vpn gateway. When vpn
it can be accessed directly from local wan
connection. This kind of usage is useful in VoIP implementation.who Draytek Support <support@draytek.com>
date September 2, 2010 17:15
Re: [Ticket # 2010082810002448] Fwd: bug in your routers
and how disable it?date September 3, 2010 7:31
Re: [Ticket # 2010082810002448] Fwd: bug in your routers
Dear sir
Sorry this mechanism cannot be changed.
Here are these feints ears at the expense of standards. And such feints, as you know, do not pass without leaving a trace. IPSEC is a very serious standard that guarantees the security of transmitted information, and here such a
PS I publish it only because I want to warn those who use these routers in production.
Source: https://habr.com/ru/post/102915/
All Articles