Reversing .Net applications. Part 0
This is the first article from the “Reversing .Net Applications” cycle, in which we will not work with MSIL, we will not remove packers and protectors, and we will not meet with obfuscated code. We will deal with all this in future articles, but for now we will touch on a few basic tools and traditionally decide simple cracks.
The current .Net platform is extremely vulnerable:
1. Programs written for .Net are compiled not into native, but into the byte-code of the .Net platform, called MSIL (MicroSoft Intermediate Language).
')
IL code is compiled immediately before launch. This technology is called Just-in-time compilation (JIT, compile on the fly).
2. All programs contain metadata.
“Metadata (metadata) is data that describes other data. In our context, it is a set of program elements of an EXE file, such as types and implementations of methods. ”
It is thanks to the metadata, or rather their special properties in the .Net environment, we can easily get the source code of the programs.
2.1 Metadata in .Net is required and universal.
“Each program in the .Net environment, in addition to MSIL code, necessarily contains metadata describing both its overall (manifest) and each type contained in it.”
2.2 Metadata in .Net is publicly available.
“Any software components and any programming tools can access the metadata.”
2.3 Metadata in .Net is exhaustive.
“Metadata contains detailed information about each type: its name, types and names of its fields, a description of properties and methods with all their parameters and return values. It also stores information about the accessibility (visibility) of all members of the class and their attributes. Metadata stores not only information about the interface of exported classes. Implementation details such as the structure of protected fields, descriptions of protected methods, and other components can also be extracted from metadata. ”
More information about the metadata structure in .Net can be read here , and in the meantime we will proceed directly to the practice. To work we need:
At the moment, in addition to the .Net reflector, there are several other popular .Net decompilers of assemblies and applications:
We will torment the "ReWrit's Crackme # 9 .Net Noob Challenge." It is quite simple, so there will be no problems with it.
Download the archive with crackme. Inside, besides the file we need, is a readme.txt with a “briefing”. Launch .Net reflector, then File -> Open -> ReWrit's Crackme # 9 noob challenge.exe, then the file opened by us will appear in the program field.
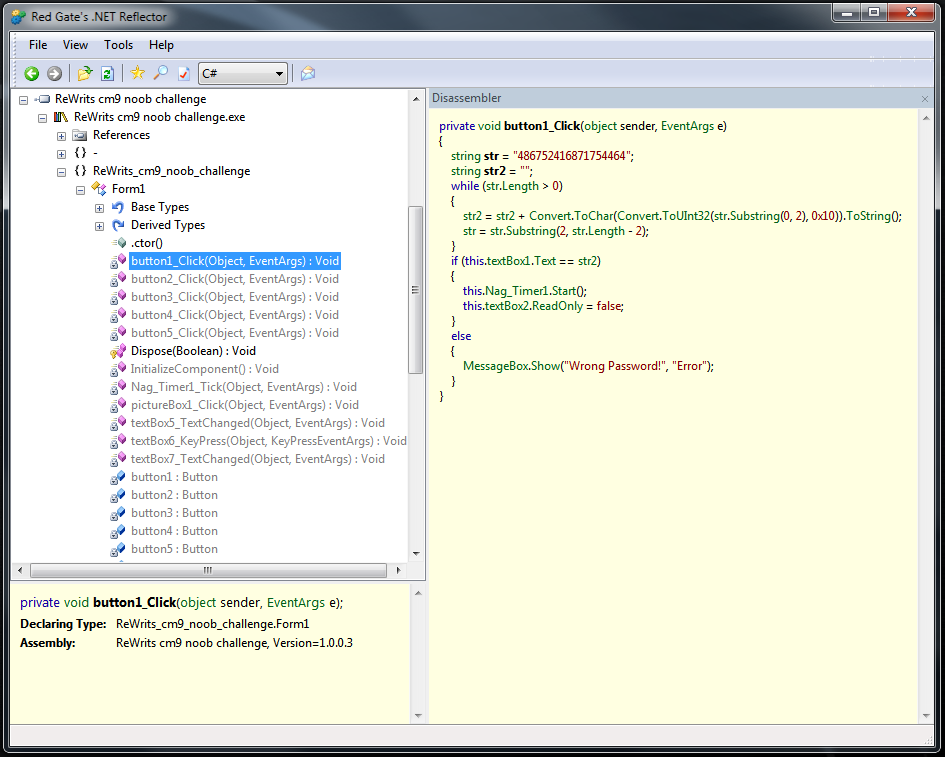
Next PKM -> Disassemble, and we are almost there.
As stated by the developer, reflector can with the same success decompile .net applications into different PLs. To verify this, select any method, and in the drop-down list, change C #, for example, to Delphi. Also reflector can be used to efficiently convert code between C # and VB.Net.
Back to our crackme, to achieve the goal there was only one step. PKM on ReWrits cm9 Noob Challenge -> Export ...
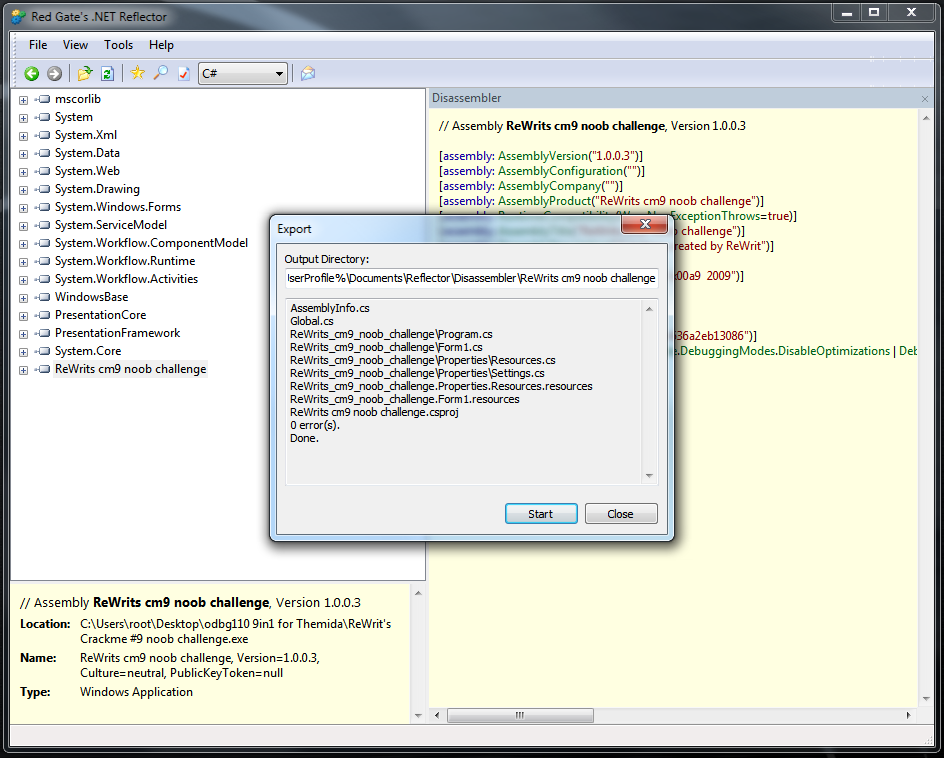
The project was exported without errors, but this is not always the case, in some cases the reflector may require the missing files or libraries. In this case, you will have to specify the path to them manually. Now we run the IDE, in my case it is Visual C # Express 2010, we open the project exported from the reflector, the studio offers to convert the project to the current version of the environment, we agree. With the move, press F5 and voila, the program works. In "combat" conditions, this is not always the case, then the reflector incorrectly exports, then the project is crookedly transformed into studios, then there is a component missing from the system. But all this does not matter if we got the lion’s share of the source code.
So, this is where the main part of the article ends. We learned why the .Net platform is so vulnerable, got acquainted with one of the many ways to get the source code of programs written for .Net, and also got the skills to work with a very powerful utility .Net Reflector. Next is the optional part, in which there will be a solution of three crackme levels, and the remaining two you have to decide on your own.
Now we can close the crack running from the studio and return to the program code. Double-click on Form1.cs and unexpectedly see the error:

but it does not scare us, click "Go to code." We focus our attention on the handlers for pushing buttons, all the most interesting things happen in them. Let's make it clear that the buttons will be called buttons, the textboxes are TB, and the messageboxes will be left alone. Run the original crackme, in it we will check the solutions obtained while we roll it up and go back to the program code. The handler for pressing the first button looks like this:
Here, the string we entered after the conversion and some operations is compared with the initially specified string, which also tolerates the conversion. If they are equal, the naga timer starts and the readonly attribute is removed from the next TB, in all others the messagebox pops up with a notification of the wrong password. Replace MessageBox.Show (“Wrong Password!”, “Error”); on MessageBox.Show (str2, "Error"); press F5, enter something into the first TB, press "OK" and get a messagebox with the correct password. We enter it in the TB of the modified program, click OK, after which the second TB will become available. But for now we are not in a hurry to enter the password into the crackme original. In the modified program, in the meantime, the timer will start, causing the naga.
Nag - an annoying window that pops up after a certain period of time (or at startup), calling for registering the program. It is found mainly in the trial programs and "trousers".
We have already jumped a few Nagas and it's time to remove them. Without closing the program, we look at the handler of the second button and see a direct comparison of the entered text with a variable containing “0x7fffffff”. The number in the variable is specified in hexadecimal form, we also need a decimal notation of this number. You can use the standard calculator. First, transfer to the "Programmer" mode (in Win7, this is the name), click "Hex", enter "0x7fffffff", poke "Dec". 2147483647 and is a password that disables the naga and gives access to the third TB. The third task I suggest you decide for yourself.
I hope that you have already decided the third task, so we can continue. The readme says that at the fourth level we have to patch the file, and we will do so. We look at the fourth button handler, without thinking twice, change “if (this.textBox6.Text == str2)” to if (this.textBox6.Text == “crack”), the password for the fourth level is crack. Fifth you have to decide for yourself.
This article ends, thank you for your attention.
The current .Net platform is extremely vulnerable:
1. Programs written for .Net are compiled not into native, but into the byte-code of the .Net platform, called MSIL (MicroSoft Intermediate Language).
')
IL code is compiled immediately before launch. This technology is called Just-in-time compilation (JIT, compile on the fly).
2. All programs contain metadata.
“Metadata (metadata) is data that describes other data. In our context, it is a set of program elements of an EXE file, such as types and implementations of methods. ”
It is thanks to the metadata, or rather their special properties in the .Net environment, we can easily get the source code of the programs.
2.1 Metadata in .Net is required and universal.
“Each program in the .Net environment, in addition to MSIL code, necessarily contains metadata describing both its overall (manifest) and each type contained in it.”
2.2 Metadata in .Net is publicly available.
“Any software components and any programming tools can access the metadata.”
2.3 Metadata in .Net is exhaustive.
“Metadata contains detailed information about each type: its name, types and names of its fields, a description of properties and methods with all their parameters and return values. It also stores information about the accessibility (visibility) of all members of the class and their attributes. Metadata stores not only information about the interface of exported classes. Implementation details such as the structure of protected fields, descriptions of protected methods, and other components can also be extracted from metadata. ”
More information about the metadata structure in .Net can be read here , and in the meantime we will proceed directly to the practice. To work we need:
- .Net reflector
- Visual C # Express (or another IDE convenient for you)
- Minimal knowledge of any PL with C-like syntax, or understanding “how it happens there” (for analyzing and editing code)
At the moment, in addition to the .Net reflector, there are several other popular .Net decompilers of assemblies and applications:
- DisSharp Decompiler (http://netdecompiler.com) - paid, in the presence of deobfuscator, the developers declare that it works several times faster than analogs. Personally, I did not like it, although I coped with several experimental programs.
- Salamander .Net decompiler (http://www.remotesoft.com/salamander/) - may have once been a competitor to the reflector, but now we will send it to the archive, Change Log ends in early 2008. Paid.
- Spices.Net Decompiler (http://www.9rays.net/Downloads.aspx) is the only one on our list that can compete with a reflector. In the presence of a good deobfuskator, code optimizer, integration with VS and other buns. Minus - paid.
- If for some reason you cannot use a reflector, there are several similar programs at your disposal, but be prepared for the fact that the result of decompilation in each of them may differ.
We will torment the "ReWrit's Crackme # 9 .Net Noob Challenge." It is quite simple, so there will be no problems with it.
Download the archive with crackme. Inside, besides the file we need, is a readme.txt with a “briefing”. Launch .Net reflector, then File -> Open -> ReWrit's Crackme # 9 noob challenge.exe, then the file opened by us will appear in the program field.

Next PKM -> Disassemble, and we are almost there.

As stated by the developer, reflector can with the same success decompile .net applications into different PLs. To verify this, select any method, and in the drop-down list, change C #, for example, to Delphi. Also reflector can be used to efficiently convert code between C # and VB.Net.
Back to our crackme, to achieve the goal there was only one step. PKM on ReWrits cm9 Noob Challenge -> Export ...

The project was exported without errors, but this is not always the case, in some cases the reflector may require the missing files or libraries. In this case, you will have to specify the path to them manually. Now we run the IDE, in my case it is Visual C # Express 2010, we open the project exported from the reflector, the studio offers to convert the project to the current version of the environment, we agree. With the move, press F5 and voila, the program works. In "combat" conditions, this is not always the case, then the reflector incorrectly exports, then the project is crookedly transformed into studios, then there is a component missing from the system. But all this does not matter if we got the lion’s share of the source code.
So, this is where the main part of the article ends. We learned why the .Net platform is so vulnerable, got acquainted with one of the many ways to get the source code of programs written for .Net, and also got the skills to work with a very powerful utility .Net Reflector. Next is the optional part, in which there will be a solution of three crackme levels, and the remaining two you have to decide on your own.
Now we can close the crack running from the studio and return to the program code. Double-click on Form1.cs and unexpectedly see the error:

but it does not scare us, click "Go to code." We focus our attention on the handlers for pushing buttons, all the most interesting things happen in them. Let's make it clear that the buttons will be called buttons, the textboxes are TB, and the messageboxes will be left alone. Run the original crackme, in it we will check the solutions obtained while we roll it up and go back to the program code. The handler for pressing the first button looks like this:
private void button1_Click(object sender, EventArgs e)
{
string str = "486752416871754464";
string str2 = "";
while (str.Length > 0)
{
str2 = str2 + Convert.ToChar(Convert.ToUInt32(str.Substring(0, 2), 0x10)).ToString();
str = str.Substring(2, str.Length - 2);
}
if (this.textBox1.Text == str2)
{
this.Nag_Timer1.Start();
this.textBox2.ReadOnly = false;
}
else
{
MessageBox.Show("Wrong Password!", "Error");
}
}
Here, the string we entered after the conversion and some operations is compared with the initially specified string, which also tolerates the conversion. If they are equal, the naga timer starts and the readonly attribute is removed from the next TB, in all others the messagebox pops up with a notification of the wrong password. Replace MessageBox.Show (“Wrong Password!”, “Error”); on MessageBox.Show (str2, "Error"); press F5, enter something into the first TB, press "OK" and get a messagebox with the correct password. We enter it in the TB of the modified program, click OK, after which the second TB will become available. But for now we are not in a hurry to enter the password into the crackme original. In the modified program, in the meantime, the timer will start, causing the naga.
Nag - an annoying window that pops up after a certain period of time (or at startup), calling for registering the program. It is found mainly in the trial programs and "trousers".
We have already jumped a few Nagas and it's time to remove them. Without closing the program, we look at the handler of the second button and see a direct comparison of the entered text with a variable containing “0x7fffffff”. The number in the variable is specified in hexadecimal form, we also need a decimal notation of this number. You can use the standard calculator. First, transfer to the "Programmer" mode (in Win7, this is the name), click "Hex", enter "0x7fffffff", poke "Dec". 2147483647 and is a password that disables the naga and gives access to the third TB. The third task I suggest you decide for yourself.
I hope that you have already decided the third task, so we can continue. The readme says that at the fourth level we have to patch the file, and we will do so. We look at the fourth button handler, without thinking twice, change “if (this.textBox6.Text == str2)” to if (this.textBox6.Text == “crack”), the password for the fourth level is crack. Fifth you have to decide for yourself.
This article ends, thank you for your attention.
Source: https://habr.com/ru/post/102750/
All Articles