Setting Group Restricted Use Policies in Windows 7
After reading the article, Windows-based computer without antivirus software , I caught fire with this idea of security and decided to try to do it myself.
Since I have Windows 7 Professional, the first idea was to use AppLocker, but it quickly turned out that he did not want to work in my edition of Windows, and requires Ultimate or Enterprise. Due to the licensing of my Windows and the emptiness of my wallet, the option with AppLocker has disappeared.
The next attempt was to configure group policies of limited use of programs. Since AppLocker is a “pumped-in” version of this mechanism, it is logical to try exactly politicians, especially since they are free for Windows users :)
Go to the settings:
gpedit.msc -> Computer Configuration -> Windows Configuration -> Security Settings -> Software Restriction Policies
')
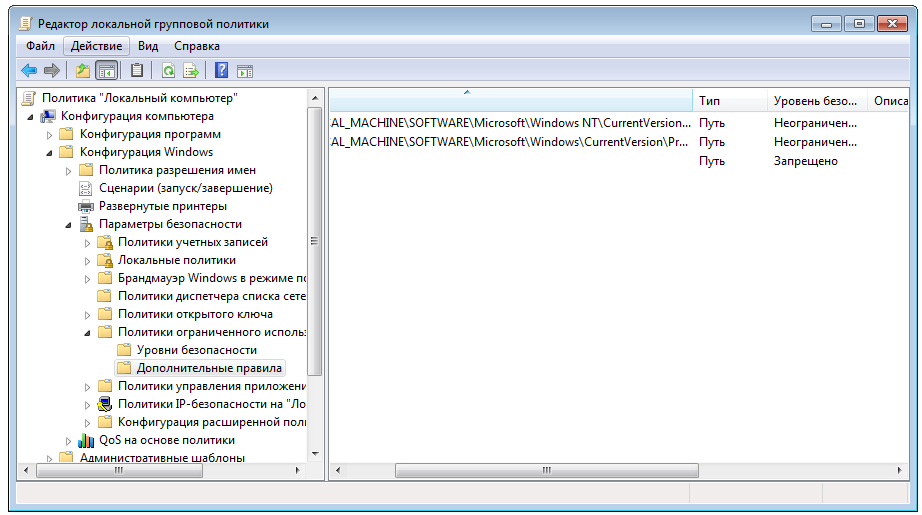
If there are no rules, the system will offer to generate automatic rules allowing the launch of programs from the Windows and Program Files folders. Also add a forbidding rule for the path * (any path). As a result, we want to be able to launch programs only from protected system folders. And what?
Yes, we will get it, but here is just a little bad luck - the shortcuts and http links do not work. You can still score on links, and it's not so good to live without labels.
If we allow the launch of files using the * .lnk mask, we will be able to create a shortcut for any executable file, and by a shortcut, start it even if it is not in the system folder. Lousy.
A request to Google leads to the following solutions: either allow launching shortcuts from a user’s folder, or use third-party bars with shortcuts. No other way. Personally, I do not like this option.
As a result, we are faced with the situation that * .lnk is, from the point of view of Windows, not a link to an executable file, but an executable file. Crazy, but what to do ... I would like the Windows to check not the location of the label, but the location of the file to which it refers.
And then I accidentally came across the settings of the list of extensions that are executable from the point of view of Windows (gpedit.msc -> Computer Configuration -> Windows Configuration -> Security Settings -> Assigned File Types). We remove LNK from there and at the same time HTTP and reloin. We get fully working labels and checking the location of the executable file.
There was a doubt whether it would be possible to pass parameters through the labels - it is possible, so everything is ok.

As a result, we got the realization of the idea described in the article “Windows-computer without antiviruses” without any inconvenience for the user.
Also for those who like to shoot themselves in the foot, you can create a folder in the Program Files and drop a shortcut for it to the desktop, calling, for example, “Sandbox”. This will allow programs to run from there without disabling policies, using a secure repository (protection via UAC).
I hope the described method will be for someone useful and new. At least I have never heard of this from anyone and have not seen it anywhere.
Source: https://habr.com/ru/post/101971/
All Articles