A study of simple crackme (part 2)
Hello, Habralyudi!
This topic is a continuation of a series of articles on the study of kryakmis ( Part 1 ). In this article we will look at the mall out of town in a more complicated way than in the previous article. The main difficulty will be in the encryption algorithm. However, anyway, it will seem too simple to many.
So let's get started.
From the tools I will only use the debugger. Here itself kryakmis.
So, traditionally run it without a debugger, enter the fake data, and look at the result:
This time there was no mesadbox. It means that we will set a breakpoint on all calls to the GetDlgItemTextA function, since it is the one responsible for “extracting” data from text fields in this case.
We set breakpoints, run the program, enter the name and serial number and click Verify. We see that bryak worked. We take a step forward, thereby allowing the function to be executed. The function was executed and the data (name) was pushed onto the stack at address 022F9C4. We trace the program before the second function call. The function was executed and the data (our serial) was pushed onto the stack at 022F8B4 address (I found this data from the arguments that go to the GetDlgItemTextA function).
Further, here in this piece of code:
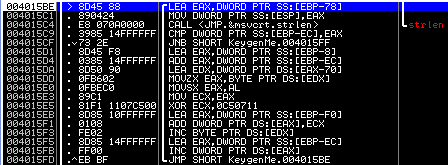
There is a procedure of modifying the name already familiar to us, in which each of its (name) symbol is replaced with the next one in the ASCII table.
')
Further the most interesting:
Here is the creation of eight sequences consisting of numbers. Further, six of them, using the function sprintf with the argument C% dr% do% dm% da% dx% dX, form such a string (n - sequence) -
C P1 r P2 o P3 m P4 A P5 x P6 X.
Then there is a procedure that replaces each character of this huge string with the symbol following the following in the ASCII table (sorry, but I don’t know how to explain this in another way). For example, there was a symbol A became C, there was 1 became 3, and so on. And in the end it turns out ready, valid serial.
The difficulty is that these lines are formed almost randomly. That is, here we see not the traditional name modification, but rather a modification of the addresses contained in the registers and the stack. Addresses change depending on the length of the name, so the names with the same length would have the same serial number if I hadn’t understood the principle of formation of which I can’t understand (it is commented). The code above is not commented by me, since it mainly contains mathematical operations that are not difficult to understand.
Name example - Myname
Example serial number: E99696;: 2t5284; 342q87;: 6458o696924: c3995: 68326z432575;: 22Z
Example name2 - name
Serial2 example - E73872238t9: 5274: q; 5257262o; 2752558c3: 72987622z3: 575886 :: Z
Examples may not work for you, just because of the random value.
Here is such an example of unsolvable keygenmy.
PS The next article will be more interesting. I will tell about manual unpacking, and about more complex encryption algorithms.
This topic is a continuation of a series of articles on the study of kryakmis ( Part 1 ). In this article we will look at the mall out of town in a more complicated way than in the previous article. The main difficulty will be in the encryption algorithm. However, anyway, it will seem too simple to many.
Required material
So let's get started.
From the tools I will only use the debugger. Here itself kryakmis.
Trial run
So, traditionally run it without a debugger, enter the fake data, and look at the result:

This time there was no mesadbox. It means that we will set a breakpoint on all calls to the GetDlgItemTextA function, since it is the one responsible for “extracting” data from text fields in this case.
Tracing
We set breakpoints, run the program, enter the name and serial number and click Verify. We see that bryak worked. We take a step forward, thereby allowing the function to be executed. The function was executed and the data (name) was pushed onto the stack at address 022F9C4. We trace the program before the second function call. The function was executed and the data (our serial) was pushed onto the stack at 022F8B4 address (I found this data from the arguments that go to the GetDlgItemTextA function).
Further, here in this piece of code:

There is a procedure of modifying the name already familiar to us, in which each of its (name) symbol is replaced with the next one in the ASCII table.
')
Main difficulty
Further the most interesting:
004015FF |> 8D45 F8 LEA EAX,DWORD PTR SS:[EBP-8]
00401602 |. 0385 14FFFFFF ADD EAX,DWORD PTR SS:[EBP-EC]
00401608 |. 83E8 70 SUB EAX,70
0040160B |. 0FBE10 MOVSX EDX,BYTE PTR DS:[EAX]
0040160E |. 8B85 10FFFFFF MOV EAX,DWORD PTR SS:[EBP-F0]
00401614 |. 31D0 XOR EAX,EDX
00401616 |. 0FBE4D EC MOVSX ECX,BYTE PTR SS:[EBP-14] // .
0040161A |. D3E0 SHL EAX,CL
0040161C |. 8B8D 14FFFFFF MOV ECX,DWORD PTR SS:[EBP-EC]
00401622 |. D3F8 SAR EAX,CL
00401624 |. 8985 0CFFFFFF MOV DWORD PTR SS:[EBP-F4],EAX
0040162A |. 8D85 10FFFFFF LEA EAX,DWORD PTR SS:[EBP-F0]
00401630 |. FF00 INC DWORD PTR DS:[EAX]
00401632 |. 8B85 0CFFFFFF MOV EAX,DWORD PTR SS:[EBP-F4]
00401638 |. 3385 10FFFFFF XOR EAX,DWORD PTR SS:[EBP-F0]
0040163E |. 894424 08 MOV DWORD PTR SS:[ESP+8],EAX
00401642 |. 8B85 0CFFFFFF MOV EAX,DWORD PTR SS:[EBP-F4]
00401648 |. 894424 04 MOV DWORD PTR SS:[ESP+4],EAX
0040164C |. 8B85 10FFFFFF MOV EAX,DWORD PTR SS:[EBP-F0]
00401652 |. 890424 MOV DWORD PTR SS:[ESP],EAX
00401655 |. E8 36FCFFFF CALL craomaxx.00401290
0040165A |. 8985 08FFFFFF MOV DWORD PTR SS:[EBP-F8],EAX
00401660 |. 8B85 0CFFFFFF MOV EAX,DWORD PTR SS:[EBP-F4]
00401666 |. 3385 10FFFFFF XOR EAX,DWORD PTR SS:[EBP-F0]
0040166C |. 894424 08 MOV DWORD PTR SS:[ESP+8],EAX
00401670 |. 8B85 0CFFFFFF MOV EAX,DWORD PTR SS:[EBP-F4]
00401676 |. 894424 04 MOV DWORD PTR SS:[ESP+4],EAX
0040167A |. 8B85 10FFFFFF MOV EAX,DWORD PTR SS:[EBP-F0]
00401680 |. 890424 MOV DWORD PTR SS:[ESP],EAX
00401683 |. E8 2EFCFFFF CALL craomaxx.004012B6
00401688 |. 8985 04FFFFFF MOV DWORD PTR SS:[EBP-FC],EAX
0040168E |. 8B85 04FFFFFF MOV EAX,DWORD PTR SS:[EBP-FC]
00401694 |. 894424 04 MOV DWORD PTR SS:[ESP+4],EAX
00401698 |. 8B85 08FFFFFF MOV EAX,DWORD PTR SS:[EBP-F8]
0040169E |. 890424 MOV DWORD PTR SS:[ESP],EAX
004016A1 |. E8 34FCFFFF CALL craomaxx.004012DA
004016A6 |. 8985 00FFFFFF MOV DWORD PTR SS:[EBP-100],EAX
004016AC |. 8B85 00FFFFFF MOV EAX,DWORD PTR SS:[EBP-100]
004016B2 |. 2385 08FFFFFF AND EAX,DWORD PTR SS:[EBP-F8]
004016B8 |. 3385 04FFFFFF XOR EAX,DWORD PTR SS:[EBP-FC]
004016BE |. 8985 FCFEFFFF MOV DWORD PTR SS:[EBP-104],EAX
004016C4 |. 8B85 00FFFFFF MOV EAX,DWORD PTR SS:[EBP-100]
004016CA |. 894424 08 MOV DWORD PTR SS:[ESP+8],EAX
004016CE |. 8B85 04FFFFFF MOV EAX,DWORD PTR SS:[EBP-FC]
004016D4 |. 894424 04 MOV DWORD PTR SS:[ESP+4],EAX
004016D8 |. 8B85 08FFFFFF MOV EAX,DWORD PTR SS:[EBP-F8]
004016DE |. 890424 MOV DWORD PTR SS:[ESP],EAX
004016E1 |. E8 D0FBFFFF CALL craomaxx.004012B6
004016E6 |. 8985 F8FEFFFF MOV DWORD PTR SS:[EBP-108],EAX
004016EC |. 8B85 F8FEFFFF MOV EAX,DWORD PTR SS:[EBP-108]
004016F2 |. 894424 0C MOV DWORD PTR SS:[ESP+C],EAX
004016F6 |. 8B85 FCFEFFFF MOV EAX,DWORD PTR SS:[EBP-104]
004016FC |. 894424 08 MOV DWORD PTR SS:[ESP+8],EAX
00401700 |. 8B85 04FFFFFF MOV EAX,DWORD PTR SS:[EBP-FC]
00401706 |. 894424 04 MOV DWORD PTR SS:[ESP+4],EAX
0040170A |. 8B85 08FFFFFF MOV EAX,DWORD PTR SS:[EBP-F8]
00401710 |. 890424 MOV DWORD PTR SS:[ESP],EAX
00401713 |. E8 DCFBFFFF CALL craomaxx.004012F4
00401718 |. 8985 F4FEFFFF MOV DWORD PTR SS:[EBP-10C],EAX
0040171E |. 8B85 10FFFFFF MOV EAX,DWORD PTR SS:[EBP-F0]
00401724 |. 890424 MOV DWORD PTR SS:[ESP],EAX
00401727 |. E8 F8FBFFFF CALL craomaxx.00401324
0040172C |. 8985 10FFFFFF MOV DWORD PTR SS:[EBP-F0],EAX
00401732 |. 8B85 0CFFFFFF MOV EAX,DWORD PTR SS:[EBP-F4]
00401738 |. 890424 MOV DWORD PTR SS:[ESP],EAX
0040173B |. E8 E4FBFFFF CALL craomaxx.00401324
00401740 |. 8985 0CFFFFFF MOV DWORD PTR SS:[EBP-F4],EAX
00401746 |. 8B85 08FFFFFF MOV EAX,DWORD PTR SS:[EBP-F8]
0040174C |. 890424 MOV DWORD PTR SS:[ESP],EAX
0040174F |. E8 D0FBFFFF CALL craomaxx.00401324
00401754 |. 8985 08FFFFFF MOV DWORD PTR SS:[EBP-F8],EAX
0040175A |. 8B85 04FFFFFF MOV EAX,DWORD PTR SS:[EBP-FC]
00401760 |. 890424 MOV DWORD PTR SS:[ESP],EAX
00401763 |. E8 BCFBFFFF CALL craomaxx.00401324
00401768 |. 8985 04FFFFFF MOV DWORD PTR SS:[EBP-FC],EAX
0040176E |. 8B85 00FFFFFF MOV EAX,DWORD PTR SS:[EBP-100]
00401774 |. 890424 MOV DWORD PTR SS:[ESP],EAX
00401777 |. E8 A8FBFFFF CALL craomaxx.00401324
0040177C |. 8985 00FFFFFF MOV DWORD PTR SS:[EBP-100],EAX
00401782 |. 8B85 F4FEFFFF MOV EAX,DWORD PTR SS:[EBP-10C]
00401788 |. 890424 MOV DWORD PTR SS:[ESP],EAX
0040178B |. E8 94FBFFFF CALL craomaxx.00401324
00401790 |. 8985 F4FEFFFF MOV DWORD PTR SS:[EBP-10C],EAX ; |
00401796 |. 8B85 F4FEFFFF MOV EAX,DWORD PTR SS:[EBP-10C] ; |
0040179C |. 894424 1C MOV DWORD PTR SS:[ESP+1C],EAX ; |
004017A0 |. 8B85 00FFFFFF MOV EAX,DWORD PTR SS:[EBP-100] ; |
004017A6 |. 894424 18 MOV DWORD PTR SS:[ESP+18],EAX ; |
004017AA |. 8B85 04FFFFFF MOV EAX,DWORD PTR SS:[EBP-FC] ; |
004017B0 |. 894424 14 MOV DWORD PTR SS:[ESP+14],EAX ; |
004017B4 |. 8B85 08FFFFFF MOV EAX,DWORD PTR SS:[EBP-F8] ; |
004017BA |. 894424 10 MOV DWORD PTR SS:[ESP+10],EAX ; |
004017BE |. 8B85 0CFFFFFF MOV EAX,DWORD PTR SS:[EBP-F4] ; |
004017C4 |. 894424 0C MOV DWORD PTR SS:[ESP+C],EAX ; |
004017C8 |. 8B85 10FFFFFF MOV EAX,DWORD PTR SS:[EBP-F0] ; |
004017CE |. 894424 08 MOV DWORD PTR SS:[ESP+8],EAX ; |
004017D2 |. C74424 04 7840>MOV DWORD PTR SS:[ESP+4],craomaxx.004040>; |ASCII "C%dr%do%dm%da%dx%dX"
004017DA |. 8D85 18FFFFFF LEA EAX,DWORD PTR SS:[EBP-E8] ; |
004017E0 |. 890424 MOV DWORD PTR SS:[ESP],EAX ; |
004017E3 |. E8 C8070000 CALL <JMP.&msvcrt.sprintf> ; \sprintf
004017E8 |. C785 14FFFFFF >MOV DWORD PTR SS:[EBP-EC],0
004017F2 |> 8D85 18FFFFFF /LEA EAX,DWORD PTR SS:[EBP-E8] ; |
004017F8 |. 890424 |MOV DWORD PTR SS:[ESP],EAX ; |
004017FB |. E8 D0070000 |CALL <JMP.&msvcrt.strlen> ; \strlen
00401800 |. 3985 14FFFFFF |CMP DWORD PTR SS:[EBP-EC],EAX
00401806 |. 73 2A |JNB SHORT craomaxx.00401832
00401808 |. 8D45 F8 |LEA EAX,DWORD PTR SS:[EBP-8]
0040180B |. 0385 14FFFFFF |ADD EAX,DWORD PTR SS:[EBP-EC]
00401811 |. 2D E0000000 |SUB EAX,0E0
00401816 |. FE00 |INC BYTE PTR DS:[EAX]
00401818 |. 8D45 F8 |LEA EAX,DWORD PTR SS:[EBP-8]
0040181B |. 0385 14FFFFFF |ADD EAX,DWORD PTR SS:[EBP-EC]
00401821 |. 2D E0000000 |SUB EAX,0E0
00401826 |. FE00 |INC BYTE PTR DS:[EAX]
00401828 |. 8D85 14FFFFFF |LEA EAX,DWORD PTR SS:[EBP-EC]
0040182E |. FF00 |INC DWORD PTR DS:[EAX]
00401830 |.^EB C0 \JMP SHORT craomaxx.004017F2
00401832 |> 8B45 08 MOV EAX,DWORD PTR SS:[EBP+8]
00401835 |. 894424 08 MOV DWORD PTR SS:[ESP+8],EAXHere is the creation of eight sequences consisting of numbers. Further, six of them, using the function sprintf with the argument C% dr% do% dm% da% dx% dX, form such a string (n - sequence) -
C P1 r P2 o P3 m P4 A P5 x P6 X.
Then there is a procedure that replaces each character of this huge string with the symbol following the following in the ASCII table (sorry, but I don’t know how to explain this in another way). For example, there was a symbol A became C, there was 1 became 3, and so on. And in the end it turns out ready, valid serial.
The difficulty is that these lines are formed almost randomly. That is, here we see not the traditional name modification, but rather a modification of the addresses contained in the registers and the stack. Addresses change depending on the length of the name, so the names with the same length would have the same serial number if I hadn’t understood the principle of formation of which I can’t understand (it is commented). The code above is not commented by me, since it mainly contains mathematical operations that are not difficult to understand.
Examples
Name example - Myname
Example serial number: E99696;: 2t5284; 342q87;: 6458o696924: c3995: 68326z432575;: 22Z
Example name2 - name
Serial2 example - E73872238t9: 5274: q; 5257262o; 2752558c3: 72987622z3: 575886 :: Z
Examples may not work for you, just because of the random value.
Here is such an example of unsolvable keygenmy.
PS The next article will be more interesting. I will tell about manual unpacking, and about more complex encryption algorithms.
Source: https://habr.com/ru/post/101047/
All Articles